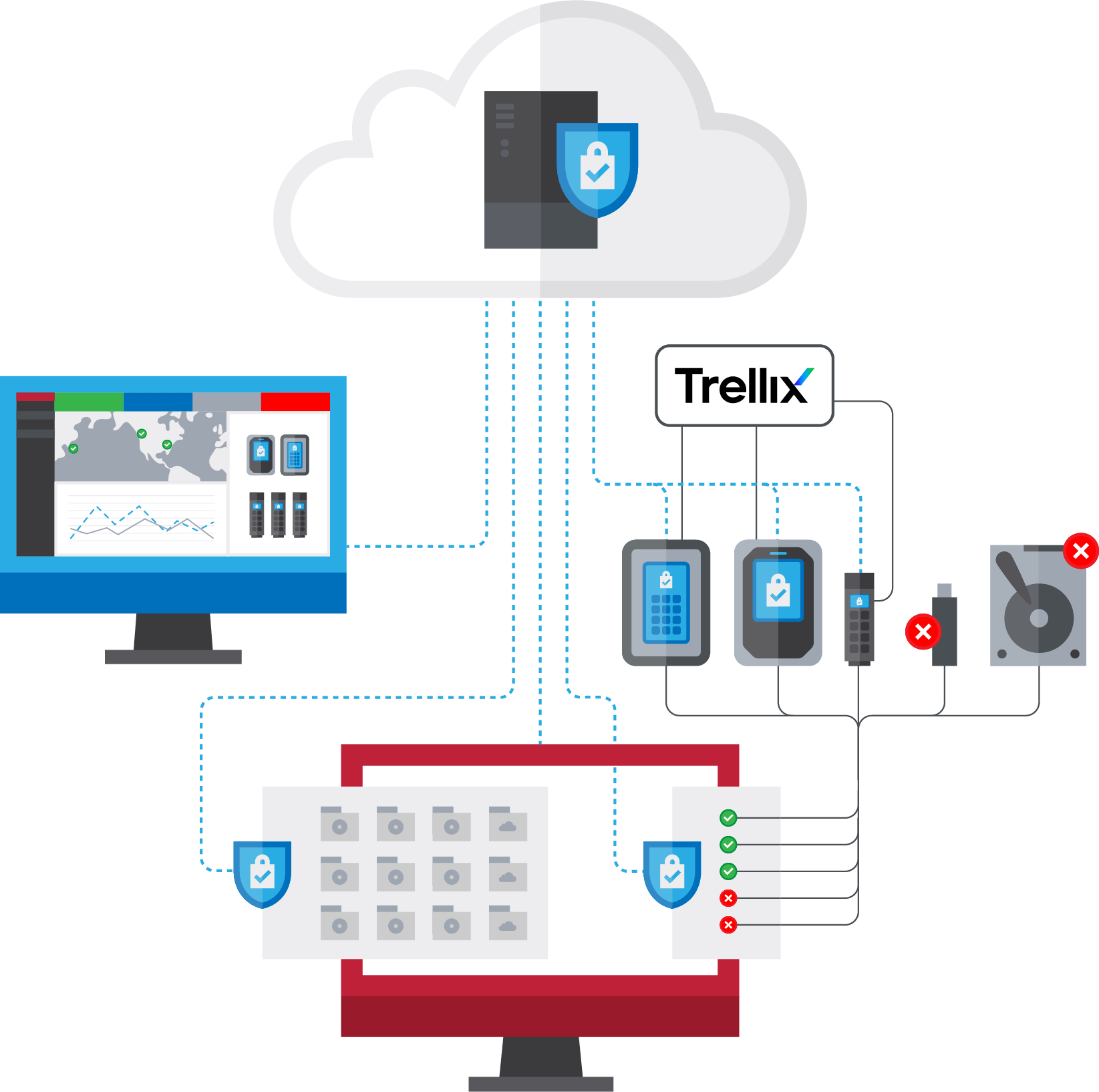
SAFECONSOLE
SIMPLE,
INTELLIGENT
REMOTE USB
DEVICE AND
PORT SECURITY
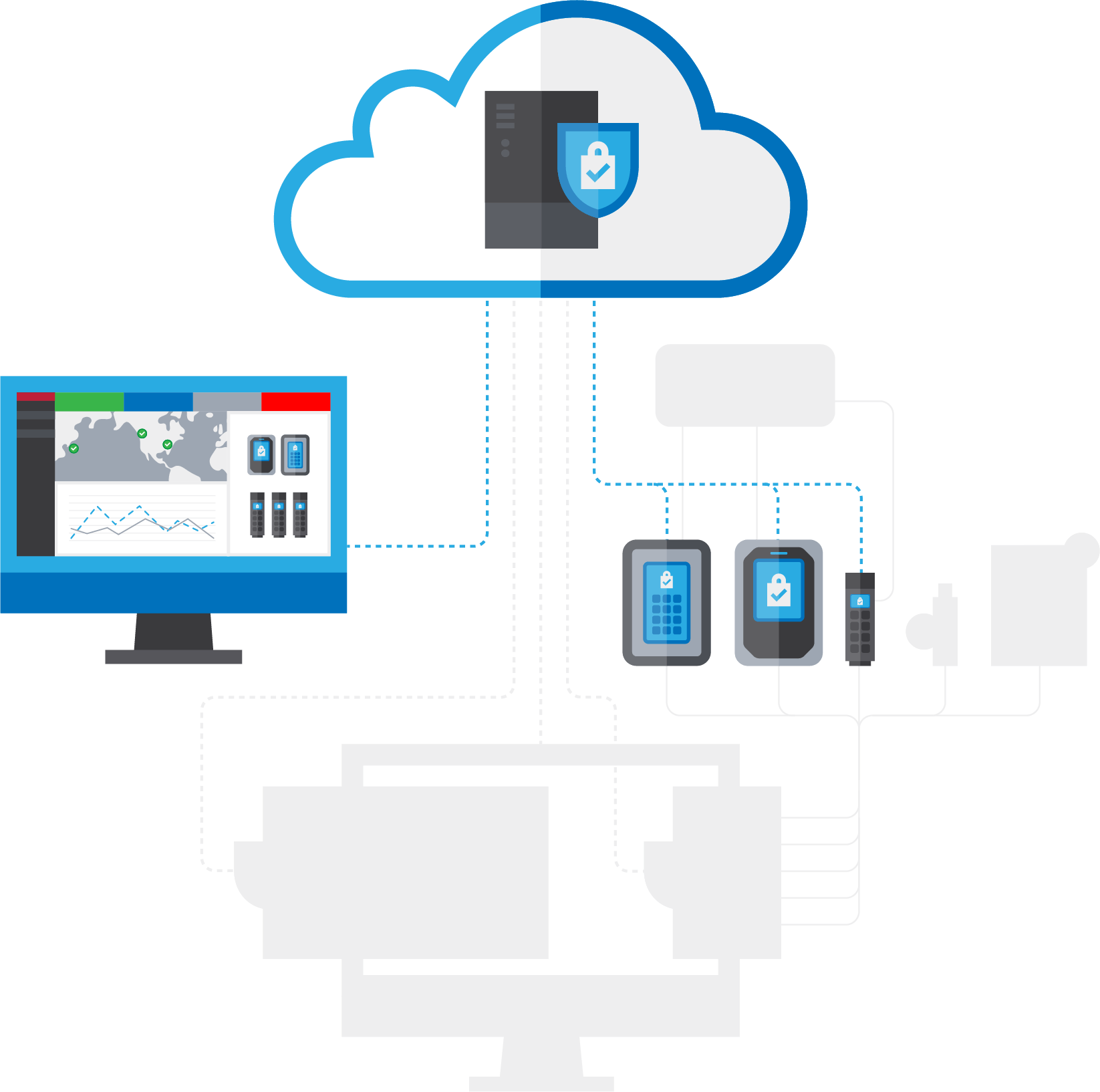
Provision, secure, manage, and audit encrypted USB drives, USB ports, and virtual folders from anywhere.
SAFECONSOLE BENEFITS
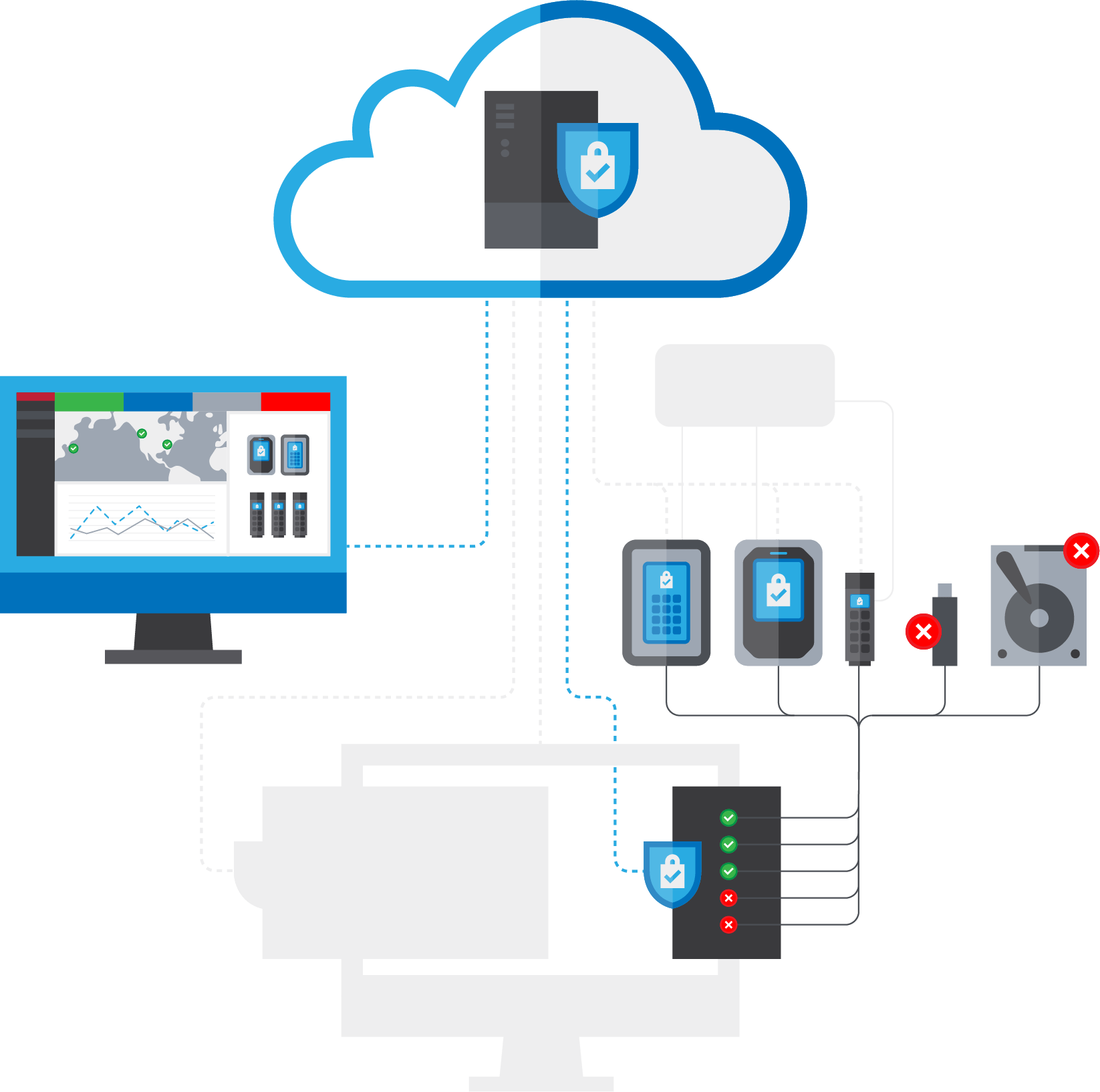
Enhance security for portable USB drives and workstation USB ports.
Reduce time spent deploying and managing secure USB drives.
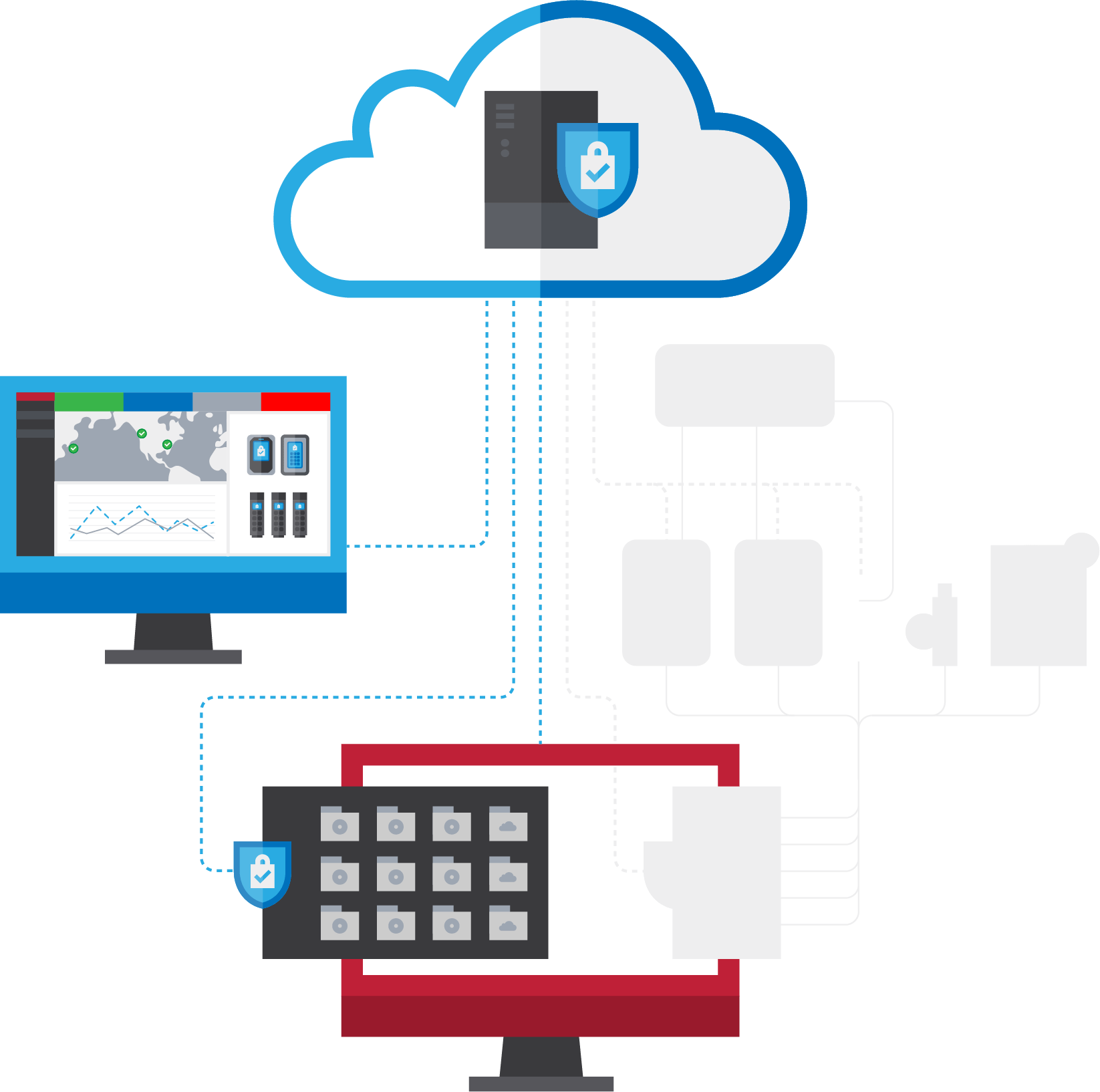
Keep data confidential by encrypting workstation data in virtual drives.
Keep your workforce productive with easy-to-use devices and dynamic security postures.
SAFECONSOLE PRODUCTS
Deployment

SafeConsole Cloud
SafeConsole Cloud is a single tenant solution, so your custom cloud hosted service is dedicated to only your organization. All network traffic is encrypted.
- Up and running in minutes. No user content is stored on the cloud
- Dedicated server can be hosted in your choice of cities around the globe (Enterprise only)
- Supports single-sign on providers including: MS Active Directory Federations Services, MS Azure, G Suite, Okta, OneLogin, PingFederate, Ping Identity (Enterprise Only)

SafeConsole On-Prem
SafeConsole On-Prem is easy to deploy if your organization requires an on-prem solution.
- Requires a dedicated Windows-based server
- Log in and manage from anywhere Administrators can authenticate to access SafeConsole with their Active Directory credentials
- Ideal for deployments of 300+ drives
GETTING STARTED

Starter Pack
Get started with SafeConsole. Mix and match SafeConsole products and get your perfect deployment. The starter pack contains 20 seats that can be used
for any product. Additional seats may be purchased separately.

Add Pro Features
Level up the basics of SafeConsole with Premium support, advance hardware replacement with RMA, Zonebuilder, and more.

Add Enterprise Features
Get all the Pro features plus SSO/SIEM integration, REST API access, dedicated servers, and more.