DataLocker: Your Trusted Partner in USB Security and Compliance Solutions
Trusted by

Trusted Encryption for USB Security and Data Protection
DataLocker offers FIPS 140-2/3 Level 3 and EAL5+ certified devices for industries demanding top compliance. All devices leverage AES 256-bit hardware encryption, tamper-resistant designs, and advanced capabilities such as on-demand cryptographic erasure, geofencing, and real-time anti-malware scanning.

Encrypted Hard Drives and External Drives
For larger data storage needs, DataLocker’s encrypted external hard drives and secure external hard drives offer robust security, combining encryption with the convenience of high-capacity storage.

Encrypted USB Drives and Secure Flash Drives
Safeguard your data with DataLocker’s military-grade encrypted USB drives, designed to meet the highest security standards and prevent unauthorized access—ideal for protecting confidential information across networks and airgaps.
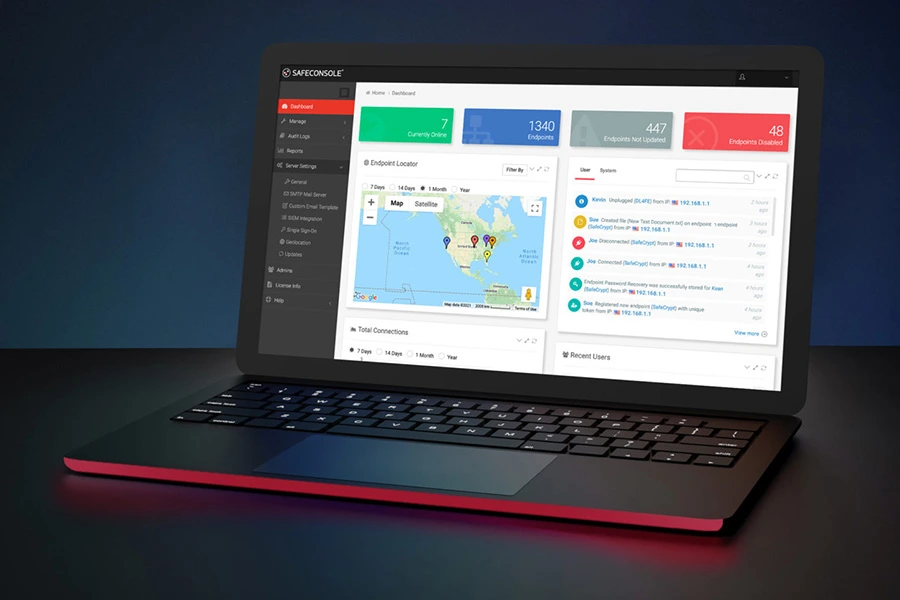
Complete Centralized Management with SafeConsole
DataLocker’s encrypted USB devices are powered by SafeConsole®, the industry’s most advanced centralized management platform, offering robust tools for complete visibility and control over your device fleet. SafeConsole is specifically designed to support organizations in meeting regulatory requirements, securing endpoints, and managing thousands of devices with ease to achieve USB security best practices.
USB Security Policy Enforcement
Set and enforce device-specific security policies such as strong passwords, usage restrictions, and file-type controls.
Comprehensive Audit Logs
Track every action taken on a device, including file access, login attempts, and geolocation data.
Remote Management
Remotely lock, wipe, and reset devices in the event of loss or theft to protect sensitive information.
Alpha Series: TAA-Compliant Webcams and Headsets
DataLocker’s Alpha Series offers TAA-compliant webcams and headsets specifically designed for secure environments, ensuring privacy and data protection in federal and high-security settings. With AlphaTalk headsets and AlphaCam H and AlphaCam H2 webcams, your organization can prevent data breaches and information leaks through audio and video devices, supporting the stringent requirements of federal agencies and enterprises where compliance and security are paramount
Industries
Manufacturing
In manufacturing, secure data transfer across air-gapped networks and operational technology (OT) systems is essential. Our encrypted solutions protect sensitive operational data and withstand the physical demands of industrial environments.
Finance
For finance and insurance sectors, secure data storage and compliance with SOX, PCI-DSS, and industry standards are crucial. Our solutions provide a secure way to handle and store confidential client data, ideal for remote work environments.
Healthcare
Healthcare organizations require encrypted solutions to protect large-format patient records and medical imaging files under HIPAA. With advanced encryption and compliance features, sensitive medical data remains secure.
Legal
Protect proprietary designs, intellectual property, and sensitive legal documents with robust encryption and centralized management. Ideal for technology and legal firms needing secure data handling across global teams.
Government & Defense
Government and defense agencies require strict compliance with standards like CMMC and NIST 800-171. Our solutions offer advanced security controls to protect classified information in diverse and regulated environments.
Education
From intellectual property to student data, educational institutions require secure storage solutions. Our encryption protects sensitive information within schools, universities, and research facilities.
Supply Chain Integrity You Can Trust
DataLocker’s commitment to security begins with a fully NATO-trusted, TAA-compliant supply chain. All components are sourced from vetted, reliable manufacturers, avoiding sanctioned entities such as Hangzhou Hualan Microelectronics Co., Ltd., which is known for potential backdoors and security risks. By maintaining a transparent supply chain free of vulnerabilities, we ensure that your data is protected from hidden threats.
 DataLocker is slick, easy to use, and reliable.
And you can quote me!
DataLocker is slick, easy to use, and reliable.
And you can quote me!




