SAFECONSOLE SAFECRYPT
Encrypt Any File, Store It Anywhere With Virtual Drives
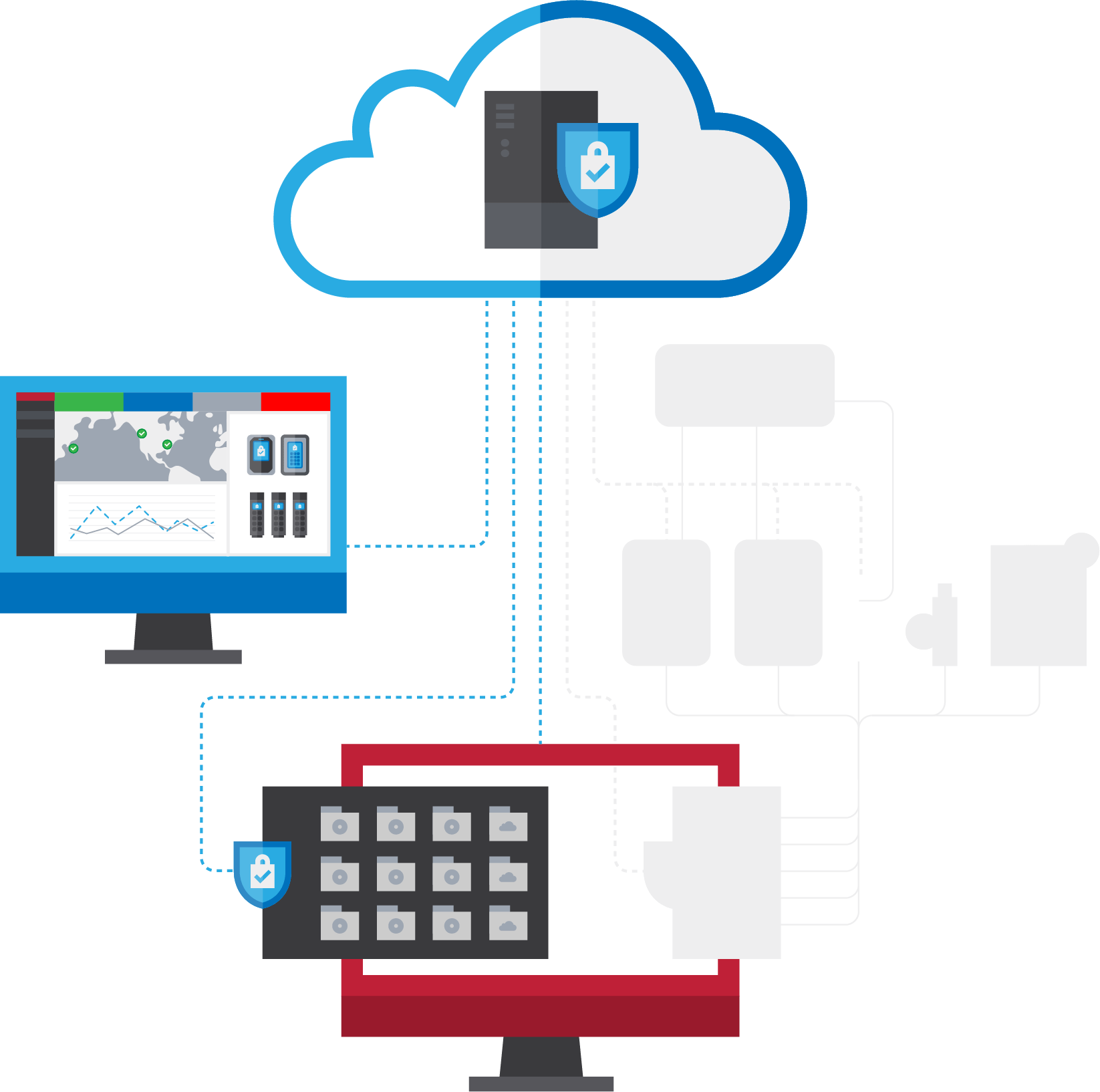
SafeCrypt allows you to encrypt files and folders while using local storage or in concert with services like Dropbox™, Google Drive™, and Microsoft OneDrive. SafeCrypt Is a Solution Managed by SafeConsole.
BENEFITS

Encryption Made Easy
Simply point your application to the SafeCrypt virtual drive letter and SafeCrypt fully encrypts your data using military grade AES 256-bit, FIPS 140-2 mode encryption before it is stored on your preferred storage endpoint.

Advanced Security
SafeCrypt offers advanced features like encrypted file names, read-only mode, file type restrictions, optional two-factor authentication, brute force attack defense, and zero knowledge software design.

Fully Compatible & Secure Virtual Drive
Windows and macOS® are supported and SafeCrypt is compatible with local files, network drives, external media such as USB flash and hard drives, and all major cloud storage providers.

Flexible and Expandable
SafeCrypt offers quick deployment, scalable storage capacities, and central management. It is the lowest cost-per-gigabyte encrypted storage solution. Store and run SafeCrypt from encrypted hard or flash drives to carry your ultra-sensitive files with you.
HOW IT WORKS
Store and secure local or cloud data in an encrypted virtual drive.
More SafeConsole Products
Remotely provision, configure, manage, and audit your fleet of encrypted USB drives, while also unlocking powerful security features for SafeConsoleReady™ drives.
Ensure that people only use approved USB devices to prevent malware intrusion or accidental file loss.