To ensure your organization’s data is kept safe, providing the users with secure USB drives is a great way to start. However, a central management solution will ensure that all risks of losing data are eliminated and provide you with powerful productivity tools while at it.
EXECUTIVE SUMMARY
A secure USB drive uses password and hardware encryption to protect your data. This technology ensures your sensitive data is always kept private and avoids data breaches. A USB drive needs to be under central management control to ensure your data is safe.
WITH THE RIGHT CENTRAL MANAGEMENT SYSTEM, YOU CAN DO THE FOLLOWING
- Limit or eliminate the risk of USB devices introducing malware onto your networks.
- Get an automatic inventory directory listing all users and their devices. As with all active inventory lists, this will limit the waste of devices and assist you when assigning previously used devices to new users.
- Enforce your security policy by ensuring that stored data is protected with a password that meets your safety standards.
- Enforce central administrator privileges on the devices and let the device user perform work in a protected user state, making the solution foolproof. The administrator decides what can be stored on and run off the devices.
- Reset forgotten passwords using a secure, local self-service or a central help desk challenge-response procedure.
- Centrally handle the state of the devices over the Internet, setting them as disabled or lost. You can even perform factory resets remotely.
- Enforce accountability and assist compliance efforts by activating an entire audit trail on all device actions and file changes.
SCENARIOS HIGHLIGHTING MANAGEMENT POSSIBILITIES
A central management system benefits users, administrators, and organizations by enabling secure USB devices to move beyond flat, secure storage and to reemerge as portable computing platforms.
Transport
A significant benefit of secure, hardware-encrypted USB drives is that you can ensure the integrity and confidentiality of the encrypted data on the drives when moving to a remote site and then re-ensure them when bringing the device back home. The security of a hardware-encrypted device cannot be deactivated, so all data is always secured and protected against tampering. The device will destroy all stored data if someone repeatedly logs in using an incorrect password. If the device is left unlocked, the hardware will lock down the device after a preset time of inactivity.
A consultant is delivering a confidential work product on a secure USB drive to a customer site. He knows that the drive’s safety technology will ensure the confidentiality of the sensitive work. He delivers his work and is handed a new batch of sensitive files. Because his USB device is foolproof, the consultant knows he can store only hardware encrypted files on the device. Upon returning to his home site, they left the customer site and noticed the device was lost in transit. The consultant immediately notifies the customer that no breach has been confirmed, but he needs a new copy of the data. The administrator at the consultancy issues a factory reset state command to the lost device, thereby erasing all the data on the device. The administrator also has the option to prompt the device to display a custom return-to-owner message.
Share
USB drives were designed to transport data. With a secure USB drive, you can safely transport select files with the assurance that your data is protected if the device is lost or stolen. A secure USB drive also safeguards against infecting customers or partners with USB malware when sharing data by ensuring that only authorized users have access to it.
A salesperson can share a presentation on a secure USB device protected with a PIN. Nothing else can run off the secure device. Anyone who wants a presentation copy can download it from the salesperson’s device and rest assured their machine’s integrity has not been violated. The main safe storage area, which houses confidential pricing strategies and quote drafts, is never exposed to the audience.
Distribute
Sometimes email is not enough, and file distribution can be both a hassle and a security risk. The right central management system for secure USB drives permits secure file distribution.
A project manager working on a sensitive project involving multiple companies is provided with a folder shortcut on his desktop. Files added to this folder will be securely distributed through a secure tunnel over the Internet onto the project team members’ authenticated, secure USB drives upon unlock.
Comply
Organizations can be strained when trying to fulfill auditing demands for compliance. When data goes beyond the network perimeter, the data audit trail often is lost. Organizations can comply with accountability and safety standards by activating full audit capabilities for device actions and file changes, even when the drives are offline and outside the network perimeter.
Work
Issuing laptops to employees who use them infrequently can be expensive. In addition, the expected hardware failure rate for the standard portable computer is 10 to 20 percent. Secure USB drives, in contrast, have a failure rate below 1 percent. Connecting your secure USB drives to a central management system will enable you to issue and maintain portable virtual workspaces on the devices centrally. This concept is often called a “managed thumb top,” It provides organizations with a low-cost option that allows users to work securely off any host computer within a company-issued, protected workspace.
As part of a contingency plan, an organization pushes out a portable virtual workspace to select users. In an emergency, such as a pandemic, the workspace will allow users to work securely from home on their unverified home computers and connect securely to the organization’s system.
Collaborate
A USB drive can be a powerful, teamwork-enhancing tool. A secure, hardware-encrypted USB drive offers benefits plus additional security. A centrally managed system automatically unlocks devices on trusted accounts, saving users and administrators time. Administrators can modify security policies to allow users to trust their teammates’ devices and computers. A user is prompted for their password if an account is not authorized.
Time is money at law firms, and USB device users at law firms may perceive security features on USB devices as roadblocks on their path to productivity and billable hours. Devices can be configured to unlock automatically, using an embedded certificate within the protected device user’s account, thus saving time and frustration. The data stored on the device will always be secure, even if the user brings the device home.
MANAGING SECURE USB DRIVES SAFEGUARDS THE INITIAL INVESTMENT
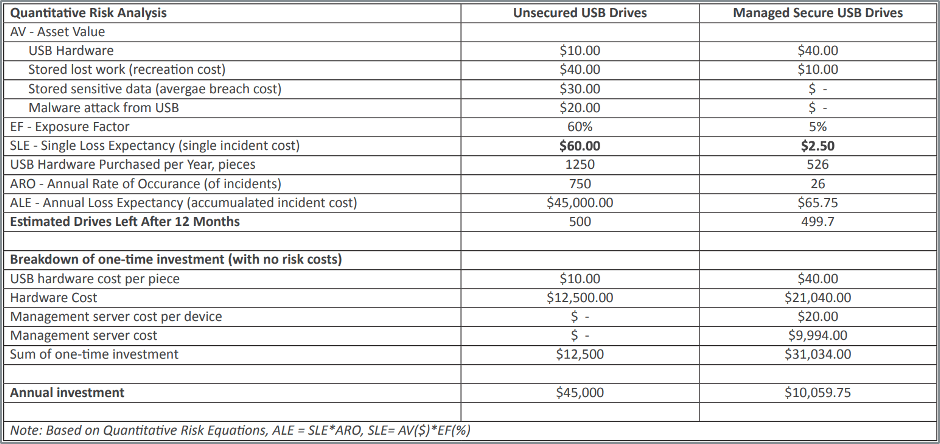
From a quantitative risk analysis perspective, a central management system provides numerous benefits. It drives down the costs of lost work by enabling backup and limits device waste by maintaining an automatic detailed inventory of every device in the network. A central management system saves organizations money and helps them improve control over and support their private data.