As cybercriminal activity rapidly progresses, threats to economic and national security are exponentially expanding. While the Defense Industrial Base (DIB) sector and the Department of Defense (DoD) supply chain continue to be prime targets, these malicious attacks jeopardize technological advantages and national security.
The DoD is working with industries to protect unclassified information within the supply chain to protect the DIB. The Office of the Under Secretary of Defense for Acquisition and Sustainment partnered with stakeholders, University Affiliated Research Centers, Federally Funded Research, and Development Centers to foster a Cybersecurity Maturity Model Certification (CMMC).
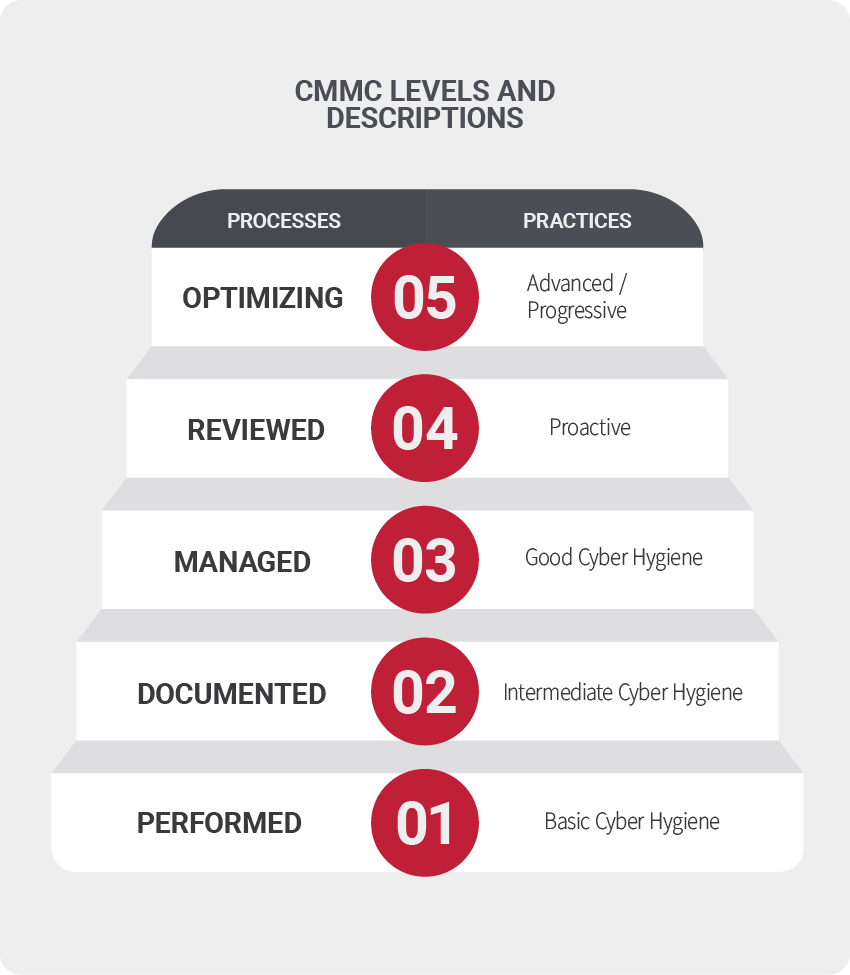
How Is the CMMC Framework Comprised?
CMMC framework consists of “maturity processes and cybersecurity best practices from multiple standards, frameworks, and other references, as well as inputs from the DIB.” The CMMC is organized by processes and practices within domains, mapping them across five security levels. Each level contains both a process and a practice that are cumulative, with each level building upon the previous. An ability to demonstrate both the processes and practices of a level is requisite for lower levels to achieve the higher one. For example, if a business wants to be a level 3, it must also meet level 1 and 2 requirements.
What Does Each Level Focus On?
1 – Safeguarding Federal Contract Information (FCI)
2 – Serve as a transition step in cybersecurity maturity progression to protect (CUI)
3 – Protect Controlled Unclassified Information (CUI)
4 & 5 – Protect CUI and reduce risk of Advanced Persistent Threats (APT’s)
Understanding Each Level

Think of Level 1 as the entry-level of cyber security for organizations that need to protect FCI. Achieving this shouldn’t be too painful for organizations currently following NIST SP 800-171 guidelines. This level is designed for Basic Cyber Hygiene and requires that organizations perform specified practices. Since many organizations will only perform these tasks when necessary and documentation might not always be needed, process maturity is not assessed for Level 1.
The focus of this level is on protecting FCI and contains practices specific to basic safeguarding requirements specified in 48 CFR 52.204-21
Examples of Basic Cyber Hygiene
- Implementing access control and authentication
- Limiting physical access to systems
- Managing visitors
- Destroying old media responsibly
- Employees using safe passwords
Processes: Performed – Performance of specified practices is required and may or may not rely on documentation. Process maturity not assessed.
Practices: Basic Cyber Hygiene – Protecting the FCI according to basic safeguarding requirements specified in 48 CFR 52.204-1.
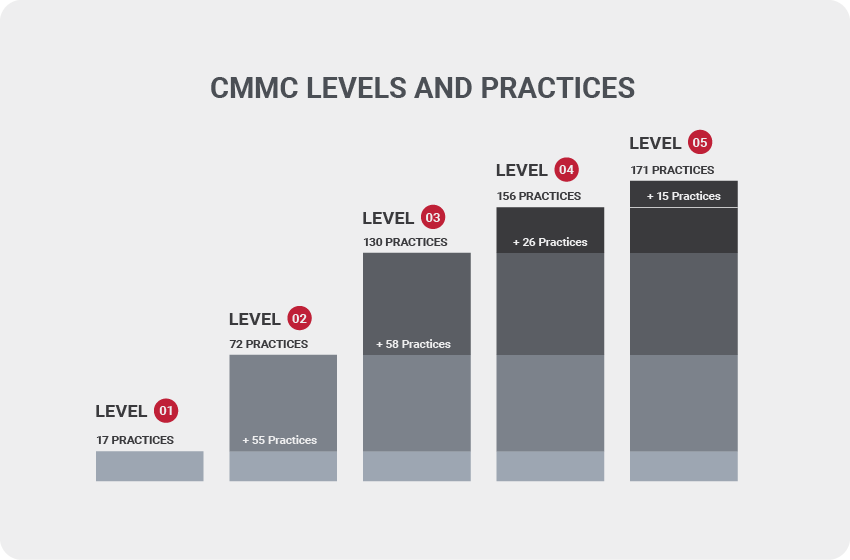
*CMMC Level 1 consists of 6 security domains addressing 9 capabilities with 17 security practices.

Generally, most businesses will need a Level 3 certification, making Level 2 essentially a transitional phase to obtain a Level 3 certification. The most significant differences in the Level 2 are the introduction of CUI protection and documentation with repeatable processes; meaning organizations must perform their processes as documented to achieve this maturity level. Additionally, organizations that want to achieve a Level 2 must first meet all the requirements of Level 1.
Examples of Documentation Implementation Processes
- Cybersecurity practices
- Cybersecurity policies
- Strategic implementation plans
- Subsets of the NIST SP 800-171 specified security processes
Processes: Documented – The requirement that organizations implementing CMMC must establish practices and policies with adequate documentation. This documentation is meant to be a repeatable process.
Practices: Intermediate Cyber Hygiene – Serves as a progression from Level 1 to 3 consisting of the NIST SP 800-171 security requirements. The protection of the CUI is also referenced.
*CMMC Level 2 consists of 15 security domains addressing 28 capabilities with additional 55 security controls.

Since only around 1% of the DOD contractors will need to achieve a Level 4 or 5, Level 3 is what the majority of the organizations will be seeking to achieve. The focus on this level is the protection of the CUI, all requirements from the NIST SP 800-171, and 20 additional practices. DFARS clause 252.20407012 applies, adding further requirements for reporting security versus what was previously in place.
Examples of Level 3 Management Practices
- Defined cybersecurity goals
- Defined missions and projects
- Resources and training
- Stakeholder involvement
- Advanced practice abilities
- Encryption of wireless communications
- Deployable encrypted, remote access
- Mobile device encryption
Processes: Managed – The requirement to establish, maintain, and implement a resource plan that demonstrates the activities of each practice. This might include missions, goals, project plans, resourcing, required training, and involvement of relevant stakeholders.
Practices: Good Cyber Hygiene – Focus is on the protection of CUI. All NIST SP 800-171 security requirements must be encompassed to mitigate threats.
*CMMC Level 3 consists of 16 security domains addressing 27 capabilities with an additional 58 security controls.

Level 4 isn’t something many organizations will need to achieve, so make sure you don’t need to go beyond Level 3 before you proceed with Level 4, which includes periodic reviews on the effectiveness of security practices. This includes corrected action when necessary and the involvement of upper management regarding the status of their information systems regularly. Level 4 practices are considered proactive and focus on protecting CUI from advanced persistent threats (APTs). However, they also encompass a subset of the requirements from the draft of NIST SP 800-172 and other documents. These practices generally improve an organization’s ability to detect and respond to security threats, especially adapting changes in the tactics, techniques, and procedures of APTs.
Practices: Reviewed – The requirement to review and measure practices for effectiveness. Corrective action and higher-level management are regularly informed on the security status.
Practices: Proactive – Focuses on protecting CUI from APT’s, comprised of NIST SP 800-171 cybersecurity best practices, to enhance detection and response capabilities of an organization to address and adapt to the changing tactics, techniques, and procedures used by APT’s
*CMMC Level 4 consists of 11 security domains addressing 16 capabilities with 26 security controls.
Level 5 is the final stage of security requirements. Level 5 obligates an organization to optimize its processes to ensure a standardized implementation across the entire organization. Practices at this level focus on protecting CUI from APTs and are considered advanced and proactive. The practices added at this level increase the sophistication and depth of the organization’s cybersecurity capabilities.
Examples of Level 5 Practices
- Proactive security measures are being taken
- Security measures exhibit optimized management
- Maintaining a cyber incident response team for security events
- Leveraging SIEM or other auditing tools
- Implement detection and intrusion systems
- Analyze network traffic
- Analyze and optimize internal security processes continually
Processes: Optimizing – The requirement of standardization and optimization process of implementation across the organization.
Practices: Advanced/Proactive – Focus on protecting CUI from APTs with additional practice to increase the depth and sophistication of cybersecurity capabilities.
*CMMC Level 1 consists of 8 security domains addressing 12 capabilities with 15 security controls.
The CMMC Level an organization needs to do business with the DoD should be stipulated in the contract. Resources, time, and energy all need to be considered when approaching any level of the CMMC requirements, and most will only need to achieve a Level 3 or lower. Due to the practices that are generally in place due to the NIST SP 800-171, it’s likely that many organizations will already have these processes and practices in place. However, this process isn’t easy and the return on investment must be considered carefully. Although the deadline isn’t solidified, these requirements will need to be implemented, most likely by the end of 2025. The sooner organizations begin establishing these protocols into their workdays, the easier the certification will be to obtain.
Looking for more information about CMMC? Subscribe to our blog for more information on CMMC and other cybersecurity topics.
References and Resources for CMMC:
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-172.pdf
https://cmmcab.org/marketplace/
https://www.acq.osd.mil/cmmc/docs/CMMC_ModelMain_V1.02_20200318.pdf
https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf
https://www.acquisition.gov/dfars
https://www.acq.osd.mil/cmmc/contact-us.html
https://www.cisa.gov/defense-industrial-base-sector