USB connectivity is the most common way to tap into the power of modern technology. From printers and portable flash drives to smartphones and tablets, transferring data between devices has never been easier. Unfortunately, this convenient accessibility acts as a double-edged sword that leaves the USB port vulnerable to a plethora of security exploits, including the dreaded ransomware attack.
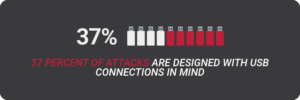
According to the 2021 Industrial Cybersecurity USB Threat Report from Honeywell, USB ports pose a significant threat to mission-critical operations. The firm estimates that 37 percent of attacks are designed with USB connections in mind, representing a nearly 100 percent increase from 2020.
Versatile and Vulnerable
A USB drive is a hacker’s dream tool. Just think about it. There is more than enough storage to accommodate malicious software, and with no defense mechanisms baked into the manufacturing process, it is essentially sold as an insecure product.
Hackers can use a USB drive’s inherited vulnerability to overwrite the firmware and hijack the device just as they would the typical PC. Of course, the big difference is the portable nature of a now weaponized mobile device with the power to cause widespread damage across unsuspecting networks.

The Need for USB Port Blocking
Organizations invest heavily in endpoint security solutions. While firewalls and anti-virus software are sufficient in thwarting external attacks, they are practically defenseless against internal threats. All it takes is one employee who doesn’t understand the risks, to unknowingly invite chaos into the equation. Once they plug a compromised flash drive into a company computer, ransomware can bypass existing security systems and gain direct endpoint access.
USB port blocking has emerged as a vital component in endpoint security. In essence, it renders readily available ports inactive to access requests, which in turn, prevents computers from running ransomware and other malware written to flash drives. By fortifying often forgotten access points, USB port blocking can form an effective last line of defense against external and internal threats alike.
Diving Deeper
USB drives are designed to reveal their specifications to the operating system. Port blocking uses this information to provide a granular level of control and provisioning. For example, administrators have the ability to allow specific USB devices while restricting access from others. They can also use whitelisting to provision access based on serial numbers and other identifiers. This level of policy enforcement extends to file privileges, enabling administrators to protect their ports from malware and safeguard confidential data in the process.
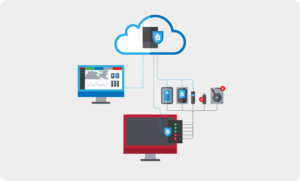
More advanced implementations of USB port blocking thrive from robust reporting capabilities. When a user attempts to insert a potentially malicious device, the blocker will not only deny access, but report the attempt to an administrator, who can then provision control accordingly. These alerts are typically archived in an activity log administrators can access from a centralized management console. Coupled with policy-based access, real-time reporting makes USB port blocking an incredibly valuable addition to any endpoint security stack.
USB Port Security Best Practices
Port blocking is essential to a well-rounded endpoint security strategy. However, it is just one way to sure up those often neglected access points. Whether it’s ransomware prevention or protecting the network from other threats, consider these pointers for hardening your USB security defenses.
Maximize native security features: There are a number of basic features that can specifically help strengthen USB port security. Don’t hesitate to use strong passwords and encryption to lock down data on compatible devices.

Keep security systems up to date: Cyber criminals are hard at work, steadily designing new ransomware strains that are even more dangerous than their predecessors. Keeping anti-malware and firewall programs up to date with the latest definitions is the best way to ensure your system is equipped to combat the rapidly evolving threat landscape.
Curb your curiosity: Considering the damage potential, a random USB drive should be viewed with the same scrutiny and caution as a live grenade. In the event that a mysterious flash drive is found on company premises, make sure the device is turned in to the IT department. The last thing you want to do is fall prey to curiosity and plug it into a networked computer.
Preach awareness: At the end of the day, prevention is the most effective weapon in any cyber security arsenal. The average person has no idea that ransomware can be loaded on to practically any type of media. Educating staff on the risks of transferring data between personal and corporate devices can go a long way in keeping those precious ports safe.
Plan for the worst: You can dot the I’s, cross the T’s and check all the traps. As history has proven, a disaster of some sort is inevitable. Whether it’s a corrupt USB drive or a malicious email attachment, a comprehensive backup plan can make you’re able to make a full recovery from any cyber security threat.
In the End
The portable nature of the digital era introduces a plethora of ways to expose confidential data to unauthorized parties. And unfortunately, the sheer volume of capable gadgets has made it alarmingly easy to overlook the potential dangers right at our fingertips. Given the proper attention, USB ports could be the among your least concerns in the battle against ransomware.