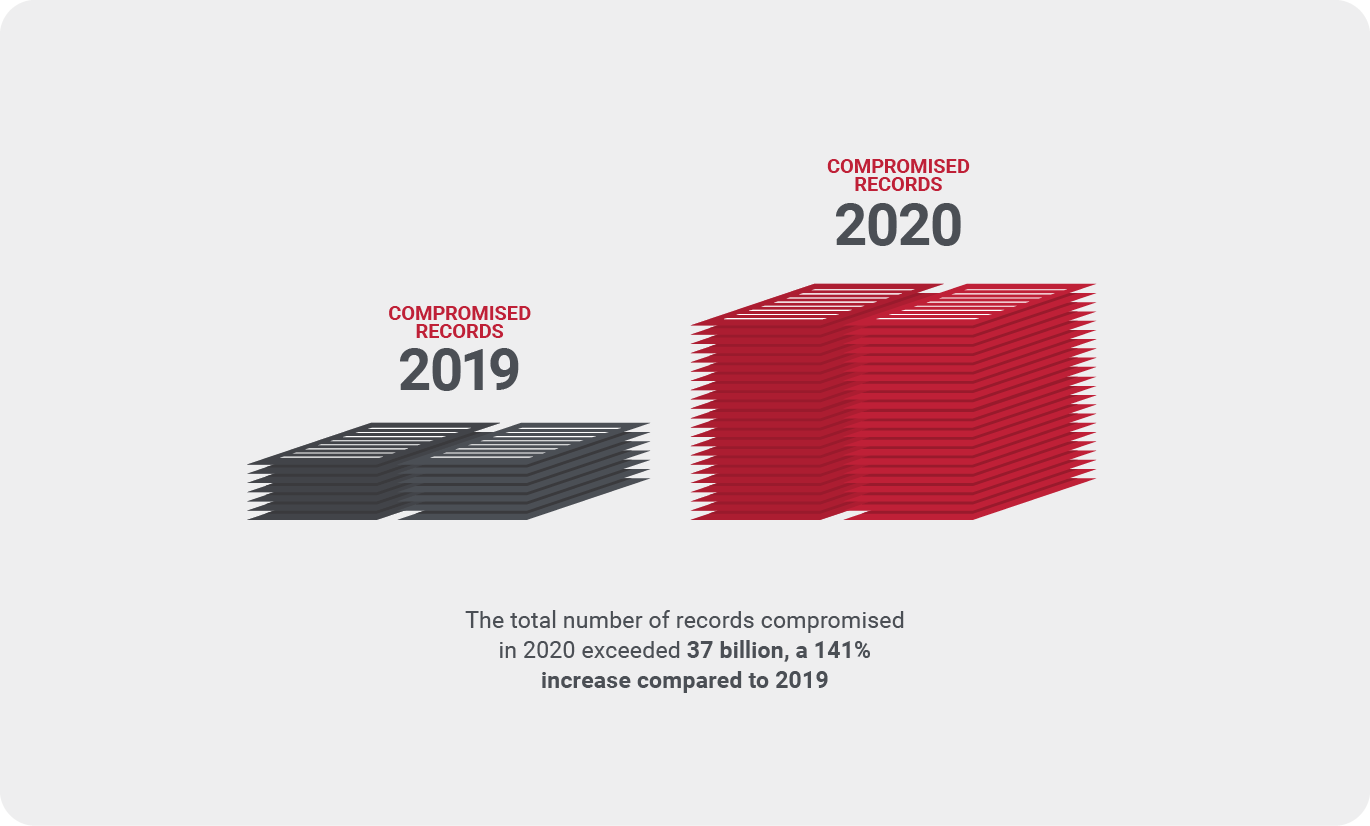
Many people assume that when information isn’t being transmitted, it’s safe. But to effectively encrypt personally identifiable information, many variables must be considered, including the state the data is in. In order to understand how to encrypt data in various states, we first need to look at the differences between the three states of data: at rest, in transit, or in use.
Encryption At Rest
Data at rest is defined as not being actively used, such as moving between devices or networks and not interacting with third parties. This information is stored in one location on hard drives, laptops, flash drives, or cloud storage. When data is encrypted at rest through hardware-based software and devices, it’s protected from people trying to access it to steal personally identifiable information or other sensitive contents. While data is generally less vulnerable at rest than in transit, often, hackers find the data at rest more valuable than data in transit because it often has a higher level of sensitive information–making this data state crucial for encryption. One thing to note: many data breaches happen due to a lost USB drive or laptop – just because data is at rest doesn’t mean it won’t move.
Encryption In Transit
Encryption in transit is when the encrypted data is active, moving between devices and networks such as the internet, within a company, or being uploaded in the cloud. When you log on to your email, your password is sent to a third party for validation–this is an example of data in transit. Encryption between audit data from devices and configuration from servers, such as with SafeConsole, helps protect it as it travels from one place to another.
Encryption In Use
When data is in use, the central processing unit of the hardware is doing something to the data, such as coding, viewing, or playing a file. Anytime a program is being updated, erased, viewed, or generated, it is considered in use. This is a difficult stage for encryption since the implementation could potentially crash or damage the application accessing the data, but is also critical to protect the information in this state as well. Although this is a tricky state to encrypt, unencrypted data in use creates a huge risk factor for data breaches.
Is Each State Encrypted The Same?
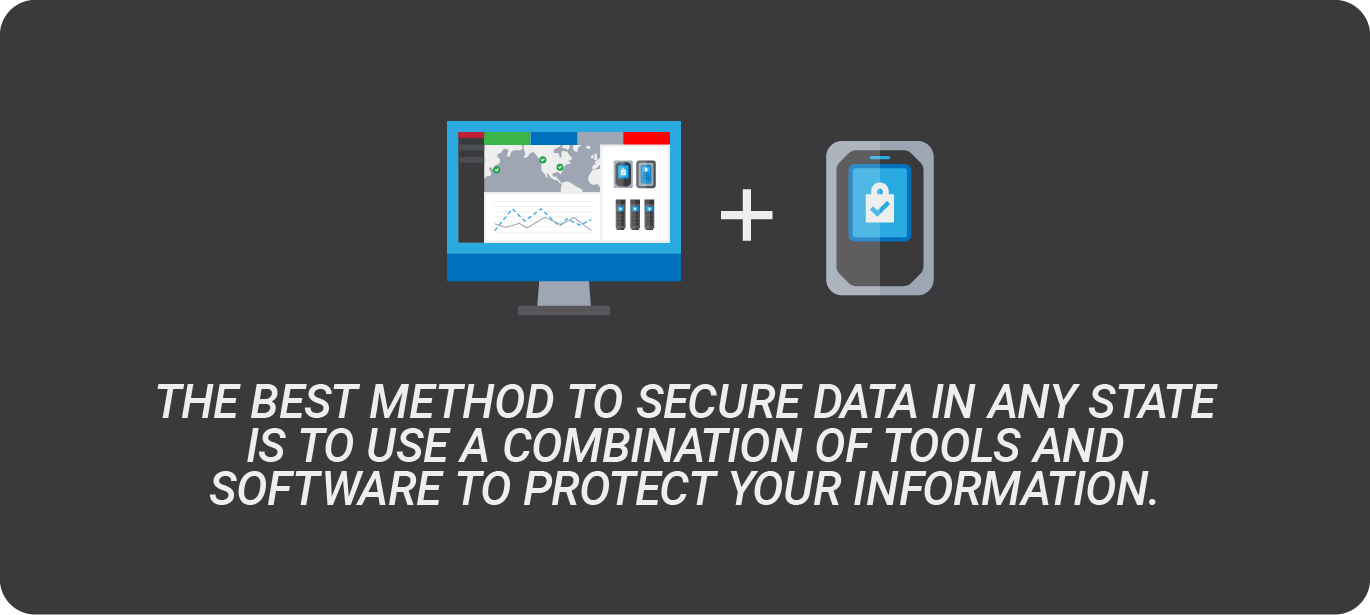
The short answer is no, but this is no straightforward answer. Each state of data needs a unique type of encryption, and there are multiple approaches to the process. The best method to secure data in any state is to use a combination of tools and software to protect your information. Speaking with an expert can help you maximize your data security and protect you for good.
We keep information everywhere and on many different devices like hard drives, laptops, tablets, smartphones, and USB drives. We also store our data on local or remote databases and in the cloud. Having so much personally identifiable information available in so many different places makes us highly susceptible to an attack. Still, the right security devices and software can help our information stay protected.
When considering encryption security, you’ll want to take a look at these tools:
- Encryption Software
- Encrypted Flash Drives
- Encrypted Hard Drives
- Encrypted Media
- Encrypted Virtual Drives
- TSL – Transport Layer Security
- SSL – Secure Sockets Layer
- S/MIME or PGP Email Encryption Tools
There are also best practices you can follow for added protection:
- Use firewalls and network access control to secure networks used to transmit data against malware and other malicious threats.
- Be proactive – not reactive. Protect your information upfront instead of waiting for an issue to occur.
- Implement encryption policies
- Classify all company data to ensure accurate levels of security are in place.
- When using any cloud services don’t rely on the company to protect your data, instead make sure you know who has access to your information, how it’s encrypted, and how often it’s backed up.
Don’t allow your business to end up as another cyber-leak statistic! Take action now to protect your data.