Endpoint Security and Control
Endpoint Security Made Simple with DataLocker
In today’s fast-paced, digital landscape, endpoints are increasingly vulnerable to data breaches, especially as remote work grows. For organizations managing sensitive information across external devices, DataLocker provides an all-in-one solution to secure data both at rest and in motion. Discover how DataLocker encrypted drives and the SafeConsole platform deliver complete control over endpoint security and data protection, empowering businesses to protect their data anytime, anywhere.
Use Case
Enhancing Endpoint Security with DataLocker Encrypted Drives and SafeConsole Management
The Challenge
Organizations need to secure data stored on employee endpoints, including external USB drives, often used by remote employees and field agents. With data frequently moving between locations, organizations face increased risks from unprotected endpoints, which account for a high percentage of successful breaches. The IT team must ensure comprehensive endpoint protection, prevent unauthorized data access, and retain control over external drives, even when off-network.
The Solution:
DataLocker Encrypted Drives and SafeConsole Endpoint Security Modules
Organizations deploy DataLocker’s encrypted USB drives across their workforce, securing endpoint data with AES 256-bit encryption. The drives provide hardware-based encryption to protect sensitive information from unauthorized access and to keep data secure even if drives are lost or stolen. Integrated with the SafeConsole management platform, these drives enable administrators to enforce consistent endpoint security policies and enhance device protection.
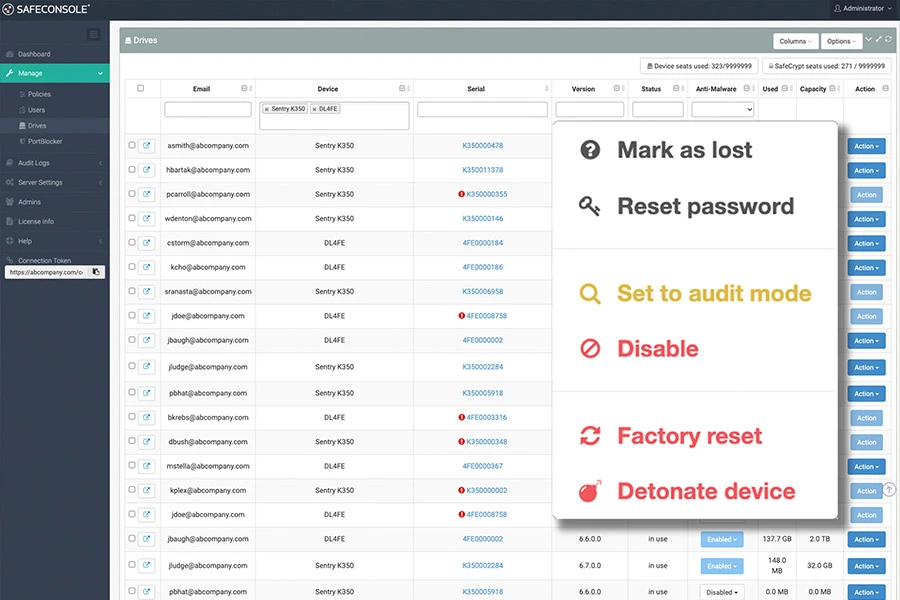
SafeConsole Secure USB Device Management
SafeConsole’s Secure USB Device Management module provides centralized control over all DataLocker encrypted drives, allowing IT teams to enforce device-specific policies across all endpoints. Administrators can manage inventory, configure password strength, and enforce retry limits to secure data both in the field and in the office. With SafeConsole’s remote capabilities, IT teams can lock, wipe, or detonate devices in case of theft, ensuring data remains protected from unauthorized access.
SafeConsole PortBlocker for Endpoint Control
The PortBlocker module in SafeConsole enhances endpoint protection by controlling USB port access on Windows and Mac devices, ensuring only authorized USB drives connect to company endpoints. By restricting unauthorized devices, PortBlocker prevents data loss and blocks potential malware from entering the network through rogue USBs. This module provides flexibility with real-time monitoring and configurable policies to meet the firm’s security standards, ensuring that only trusted DataLocker drives are used across the organization.


SafeConsole Anti-Malware for Real-Time Threat Protection
SafeConsole’s Anti-Malware module, powered by Trellix™, offers real-time malware scanning on all managed USB drives, providing additional security for data at endpoints. The module automatically scans each file added to the drives, quarantining or removing threats before they reach company systems. This proactive malware defense not only protects sensitive data but also mitigates the risk of malicious files entering through portable storage, making the endpoints safer and compliant with strict industry standards.
Results
By leveraging DataLocker encrypted drives and the SafeConsole platform, organizations gain complete control over endpoint security for data both in motion and at rest. Data remains encrypted and protected on USB drives, while SafeConsole’s Secure USB Device Management, PortBlocker, and Antimalware modules provide a comprehensive security framework:
Secure Endpoint Access
Only authorized USB devices connect to endpoints, blocking unauthorized access and reducing data breach risks.
Remote Management
IT administrators can lock, wipe, or update USB drives in real-time, protecting data even when devices are off-network.
Active Malware Protection
Built-in malware scanning identifies and isolates threats before they can compromise endpoint security.

Why DataLocker?
DataLocker specializes in data protection and endpoint security solutions for organizations that handle critical data. With our encrypted drives and SafeConsole management platform, businesses can implement comprehensive endpoint security that includes advanced encryption, remote management, malware protection, and USB port control. DataLocker delivers a robust, easy-to-manage solution to keep your data secure, compliant, and accessible.
SafeConsole Central Management
SafeConsole provides centralized management that enhances data protection and endpoint control across all DataLocker devices. With modules for secure USB device management, PortBlocker, and Antimalware, SafeConsole empowers IT administrators to monitor, manage, and secure endpoints from a single console.
Secure USB Device Management
Enforce security policies, monitor usage, and remotely lock or wipe drives in real-time.
PortBlocker
Control USB access on endpoints, allowing only approved USB devices to connect, preventing unauthorized data transfers and malware risks.
Anti-Malware Protection
Protects endpoints with real-time scanning, ensuring that files on USB drives remain malware-free and secure.
Trusted by
