Encryption is critical to protecting sensitive information. A lack of encryption has led to massive data breaches, including a Microsoft customer support database of over 280 million customer records, a 500K breach of Zoom accounts, and much more. In previous articles, we shared the basics of encryption, but you also need to know about the different types of encryption. Today, we’ll explore two basic approaches to encryption and how they can work together to create bulletproof security for various use cases.
Symmetric vs. Asymmetric
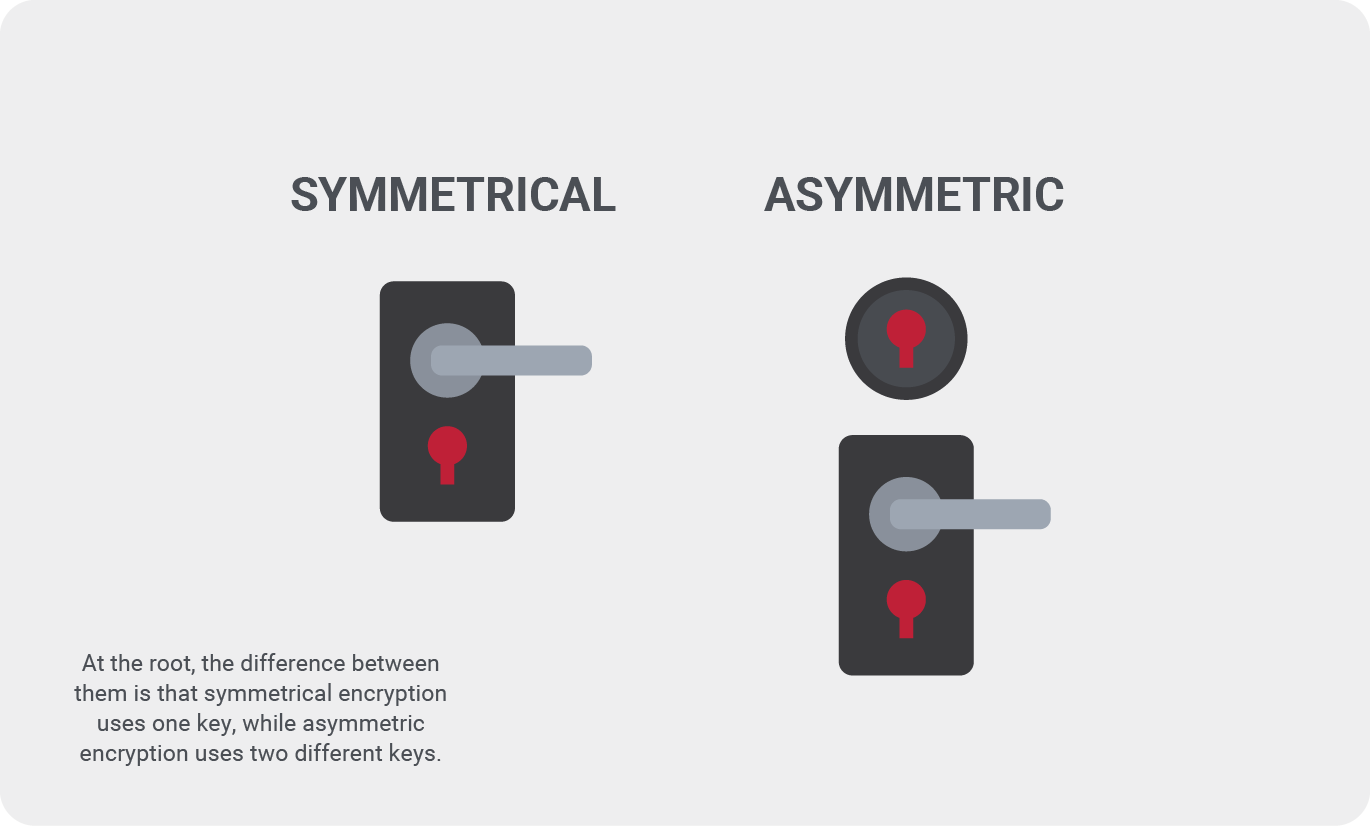
In cryptography, there are two types of encryption used: symmetric and asymmetric. At the root, the difference between them is that symmetrical encryption uses one key, while asymmetric encryption uses two different keys. A simplified way to think about it is to picture two homes with different locks on the door: one with a primary lock and a deadbolt (asymmetric) and one with only one lock (symmetric). The house with one lock only requires one key to open the door. The home with two locks has two separate keys, and both are necessary to open the door. Based on the visualization of the doors alone, it’s not difficult to determine which set of locks would be more challenging to break into.
Understanding the Types of Keys
A cryptographic key is a mathematical permutation used to take decipherable human data known as plaintext and scramble the information into unreadable information known as ciphertext.
Symmetrical encryption uses the same cryptographic key to both encrypt and decrypt information. The data is encrypted before sending, and the receiving side will use the same key to decode the information.
Asymmetric encryption uses two different cryptographic keys: a public key as well as a private key. Each participant in a conversation needs their private key, and then they also need their intended recipient’s public keys. In this type of encryption, both keys are required to transact the data. The public key is usually accessible to everyone and is often attached to a certificate with the owner’s information and a few details about the key. The private key is heavily protected and is the only way to decrypt the data that has been encrypted with the matching public key The private key is used to create the public key, but the private key cannot be recreated using the public key.

Is One Better Than The Other?
Symmetric encryption is secure as long as the key stays safe. The benefits of using this type of encryption are that it’s fast, easy, and uses minimal resources. Due to the speed, ease, and level of security, symmetric encryption is often used for local data. Symmetric encryption is mainly used when data is at rest – meaning it’s not currently being used or transmitted and is stored in devices like laptops, hard drives, flash drives, etc. Banks and payment services frequently use symmetric encryption because of its high speed and ability to quickly decrypt a large amount of data. The challenge is that the more people with access to the key, the more potential for the information to be compromised.
Asymmetric encryption is an excellent choice for protecting information due to its high level of security, although it’s much slower than symmetric encryption. Asymmetric encryption is often used for smaller amounts of information, such as private messaging or exchanging private symmetric encryption keys, and as a way to authenticate identities. Asymmetric encryption is also used to address the vulnerabilities of symmetric encryption. Digital signatures, cryptocurrency verification, and PKI or Public Key Infrastructure are other applications that, for some part, rely on asymmetric encryption

Generally, the most secure forms of encryption use both symmetric and asymmetric encryption together. This partnership creates an outstanding balance of security, speed, and performance and is the best way to protect personally identifiable information.
To learn more about how you can protect your data explore DataLocker’s encrypted devices. Not sure where to start? Schedule a demo, and we can help you find the best products and services to protect your data.