Solutions By Use Case
Tailored Solutions for Your Security Challenges
Solutions by Use Case
DataLocker’s encryption and data management solutions are designed to address a wide range of security needs across industries. Whether your focus is compliance, securing data in motion and at rest, endpoint control, or creating a robust local backup strategy, our solutions provide the tools you need to protect sensitive information and maintain control. Explore how DataLocker can help meet your specific use case with simplicity and confidence.
Compliance
Meet and Exceed Regulatory Standards
DataLocker’s FIPS-certified encrypted drives and SafeConsole platform ensure your organization meets strict compliance requirements like HIPAA, GDPR, and CMMC. With centralized management and detailed audit trails, staying compliant has never been easier.
Data in Motion and Data at Rest
Secure Data Wherever It Travels or Resides
Protect sensitive data with military-grade AES encryption, whether it’s stored onsite or in transit. DataLocker’s solutions ensure data integrity and confidentiality at all times, giving you peace of mind.
Endpoint Security and Control
Manage and Protect Every Device
With SafeConsole, administrators can enforce security policies, monitor device activity, and remotely lock or wipe drives. DataLocker solutions ensure comprehensive control over endpoints to minimize risks and prevent data breaches.
Local Backup Strategy
Secure Backup for Long-Term Protection
Safeguard critical information with encrypted local storage solutions. DataLocker drives provide a reliable and secure option for creating backups that protect against data loss, theft, or unauthorized access.
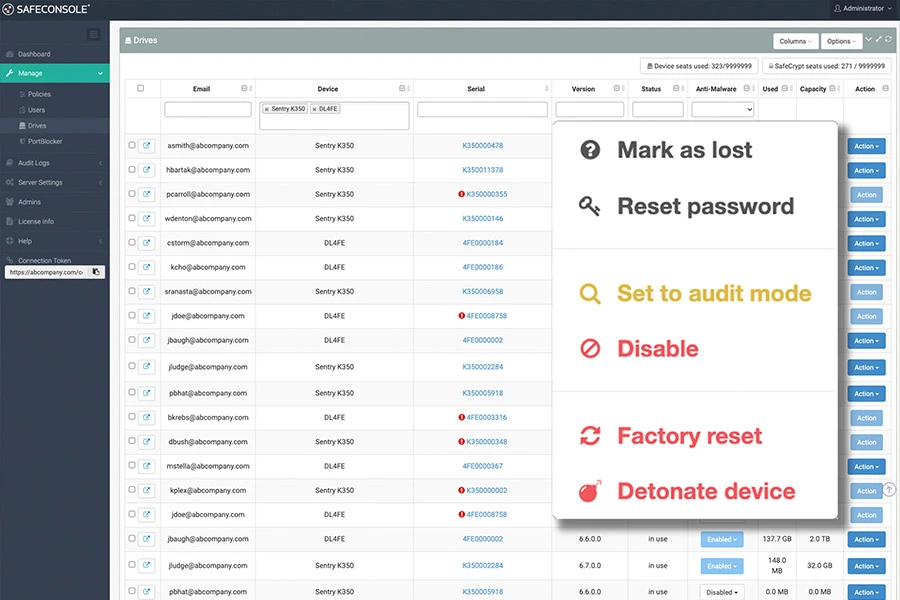
SafeConsole Platform: Centralized Device Management
Streamline security and compliance with SafeConsole.
Manage, monitor, and secure your encrypted devices with SafeConsole. This powerful platform enables remote management, policy enforcement, auditing, and more—helping you maintain control over your data while ensuring compliance with industry regulations. Discover how SafeConsole enhances your data protection strategy.
Encrypted Drives: Secure Your Data Anywhere
Protect sensitive information with military-grade encryption.
DataLocker’s encrypted drives provide robust security for your data, whether stored or in transit. With features like AES 256-bit encryption, FIPS certifications, and tamper-resistant designs, our drives are ideal for safeguarding sensitive information in any environment. Explore solutions tailored to your industry.

Trusted by
