Secure USB Device Management
SafeConsole Secure USB Device Management: Key Benefits
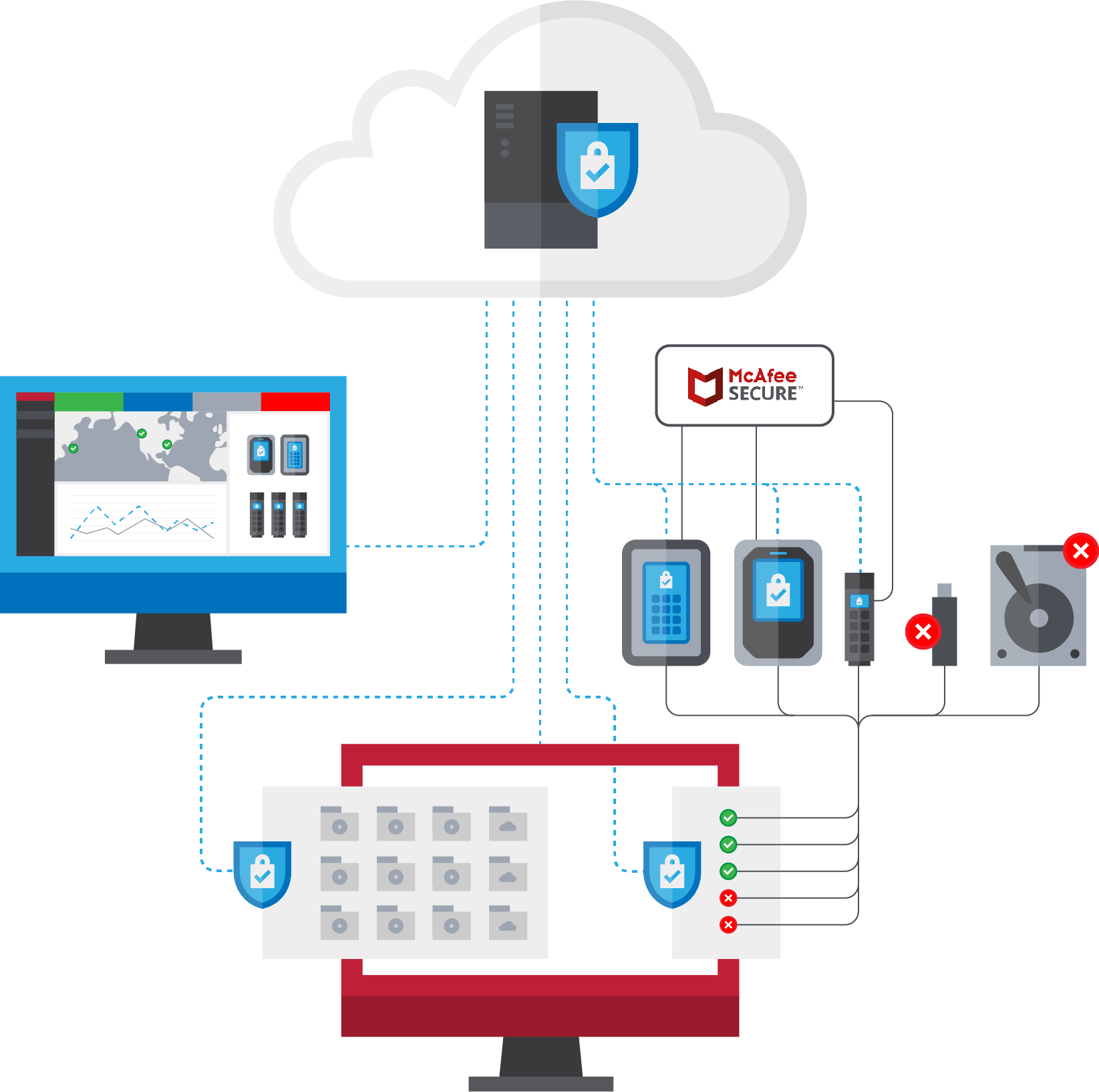
SafeConsole Secure USB Device Management allows you to manage, secure, and monitor your fleet of hardware encrypted USB drives, ensuring maximum data protection and regulatory compliance. With SafeConsole Secure USB Device Management, you can enforce strong security policies, prevent data loss, and maintain full control over all SafeConsoleReady™ devices in your organization.
Password Management
Remotely reset passwords without data loss using recovery codes, keeping the process secure against social engineering threats by flexibly employing alternative communication channels and identity proofing.
Compliance & Detailed Auditing
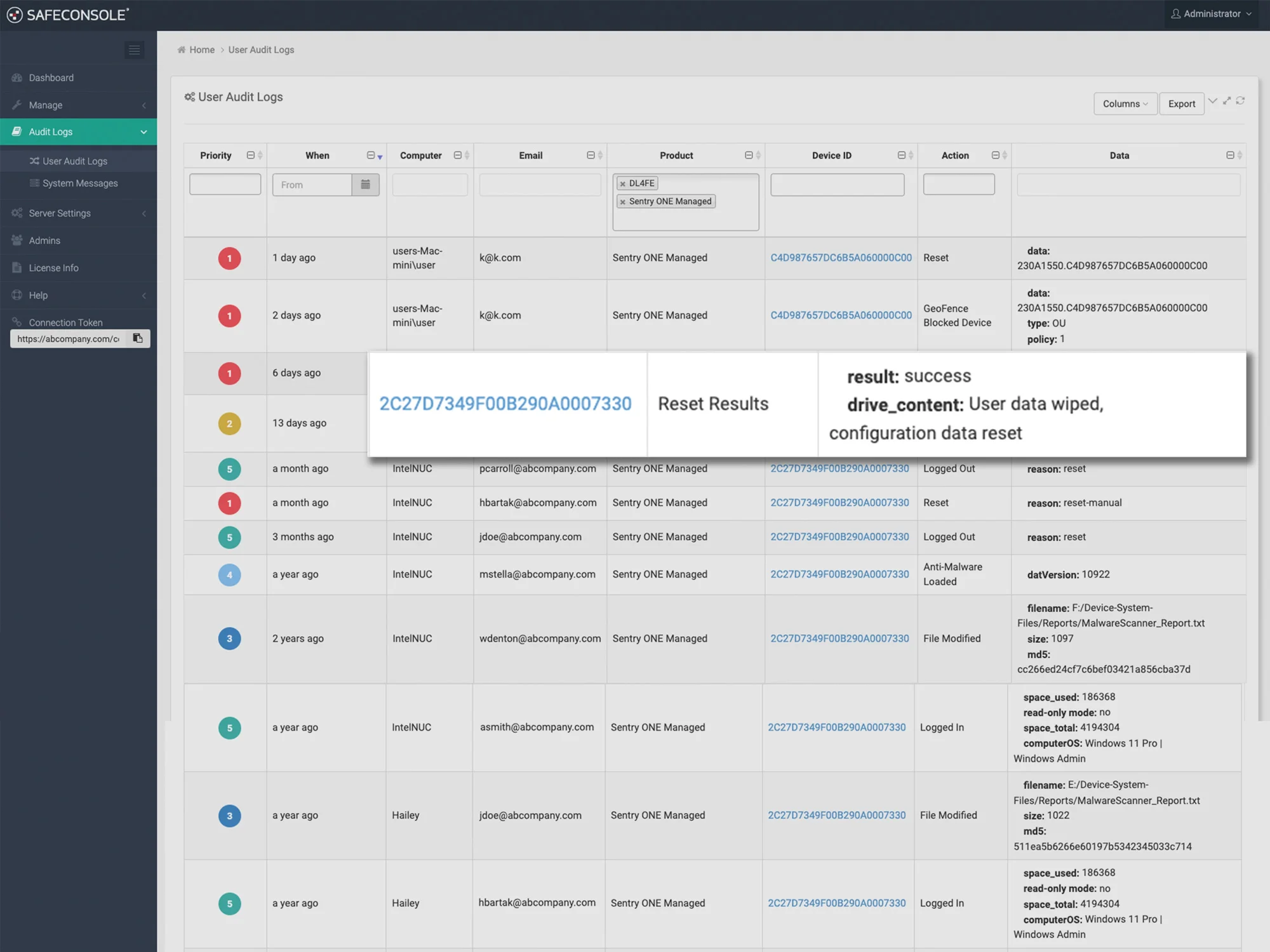
Meet compliance requirements with an up to date device inventory asset management list with detailed file auditing, tracking files that are copied, deleted, or renamed on encrypted USB drives.
Device State Management
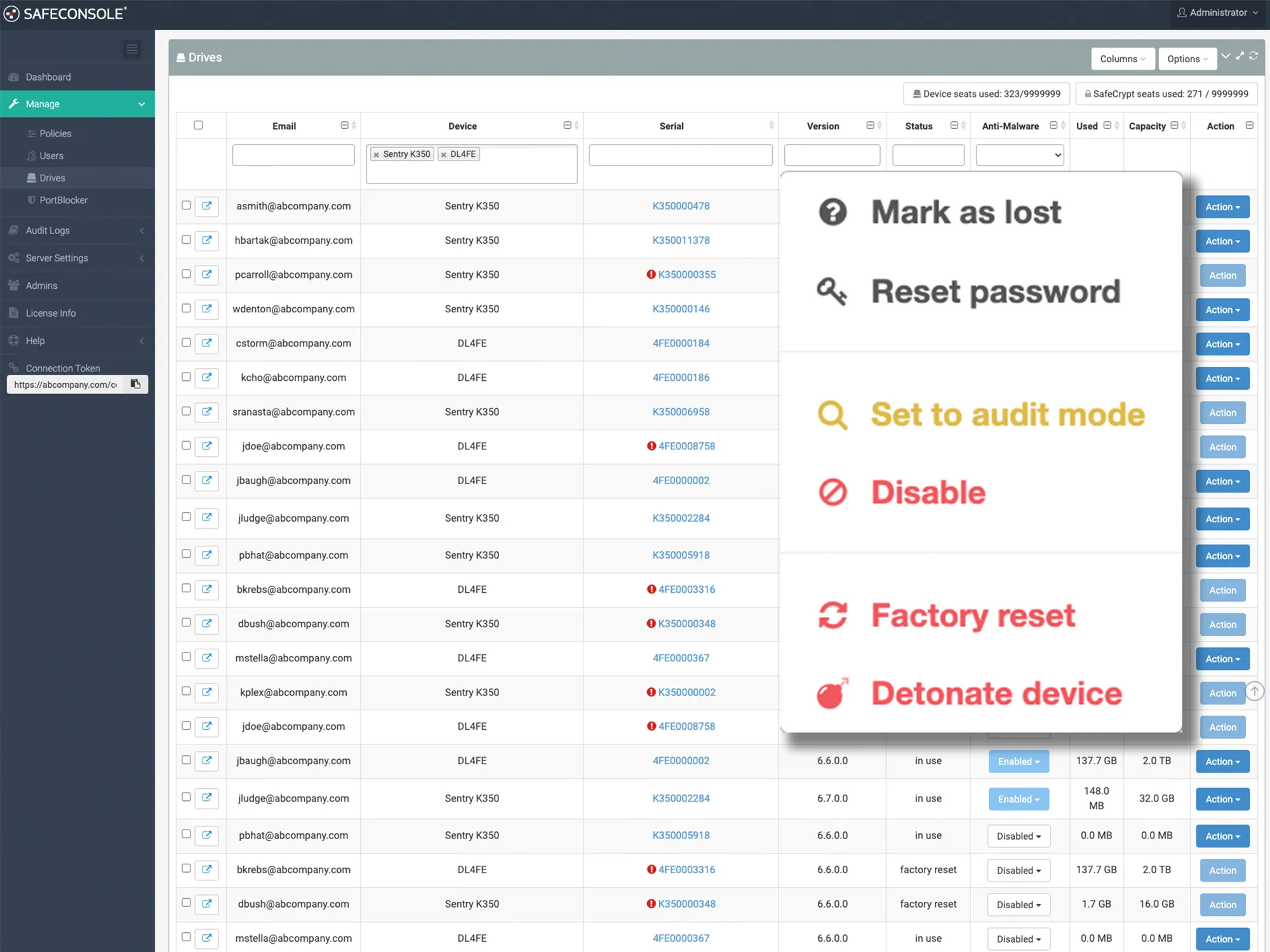
Remotely disable, kill, or recover rogue drives. In case of a lost or stolen USB drive, you can instantly disable access and wipe the device to protect your organization’s sensitive data.
File-Type Restrictions & Write Protection
Restrict which file types can be saved on your encrypted USB drives, ensuring rogue files like executable or MP3 files are not stored. With write protection, users can lock drives in read-only mode to prevent malware from copying files when using an untrusted machine.
Geolocation & Geofencing
Track the physical location of your encrypted USB drives and restrict device access by geographic location using geofencing. Ensure your drives are only accessible within predefined zones for maximum security.
ZoneBuilder – Create Trusted Zones
SafeConsole’s ZoneBuilder lets you create trusted computer zones where encrypted USB devices unlock automatically without passwords, streamlining secure file sharing. You can also restrict device access to these zones, adding an extra layer of security alongside the device password.
Comprehensive Security and Encryption
SafeConsole provides robust security features to enforce encryption policies and safeguard sensitive data across all USB devices, ensuring compliance and control.
- USB Drive Encryption & Policy Enforcement: Protect USB drives with AES 256-bit encryption, enforce password rules, and apply file-type and geolocation restrictions for enhanced security.
- Secure Password Management: Reset forgotten passwords securely with a hardware-validated, cryptographic method, fully logged for compliance without sharing master passwords.
- Policy-Driven Authentication: Strengthen security with additional authentication factors like certificates, 2FA, or SSO, ensuring admin and user accountability.
Efficient Deployment and Device Control
SafeConsole simplifies device setup and remote management, ensuring that organizations can deploy and monitor their secure USB devices with ease and flexibility.
- Zero-Touch Deployment & Enrollment: Set up devices seamlessly through end-user self-enrollment or batch configuration with DeviceDeployer, ready for use straight from the box.
- Remote Management & Control: Remotely enforce settings, activate read-only mode, update software, or perform remote wipe for lost or compromised devices.
- Real-Time Monitoring & Reporting: Track all USB activity with detailed audit logs and advanced reporting, integrating with SIEM solutions like Splunk or Graylog for enhanced visibility.
Industry Use Cases
The DataLocker SafeConsole Platform with Secure USB Device Management serves as the perfect solution across multiple industries:
Government Agencies
Challenge: Securing classified information on portable storage devices across multiple departments.
Solution: SafeConsole enables government agencies to deploy and monitor encrypted USB drives with features like geolocation tracking, automatic read-only mode activation, and remote device wiping, ensuring strict compliance with federal data security regulations.
Healthcare Organizations
Challenge: Protecting sensitive patient data while ensuring compliance with regulations like HIPAA.
Solution: SafeConsole allows healthcare providers to manage encrypted USB drives remotely, enforce password policies, restrict unauthorized file types, and instantly wipe lost drives to prevent data breaches. Geofencing ensures devices are only accessible within secure hospital networks.
Financial Institutions
Challenge: Managing encrypted USB drives used to transport sensitive financial data securely across global offices.
Solution: SafeConsole provides centralized control for USB devices, enabling real-time auditing of file transfers and ensuring compliance with PCI-DSS and GDPR. Password resets and device state management features prevent downtime and reduce security risks.
Trusted by

Customer Testimonials for SafeConsole Secure USB Device Management
Secure USB Device Management Pricing
Gain comprehensive control and security for your USB-connected devices with SafeConsole licenses.
- Full Control: Remotely manage device settings, enforce policies, and perform secure wipes for lost or stolen drives.
- Enhanced Security: Protect sensitive data with AES 256-bit encryption and centralized management.
- Compliance Ready: Ensure regulatory compliance with detailed auditing and monitoring capabilities.
$39.00/Device/Yr
Contact us for volume discounts and multi-year options!
Explore Additional SafeConsole Modules
Enhance your USB security with additional SafeConsole products designed to provide complete USB device management:
Anti-Malware for Managed Secure USB Devices
Protect your USB drives with onboard anti-malware that scans and reports malware threats directly to SafeConsole.
PortBlocker USB DLP Endpoint Protection
Prevent unauthorized USB devices from accessing your network with PortBlocker’s robust endpoint security.
SafeCrypt Client-Side Encryption Software for Cloud
Protect your sensitive data by encrypting files before uploading them to local or cloud storage.
Frequently Asked Questions (FAQ)
What is SafeConsole Secure USB Device Management?
SafeConsole Secure USB Device Management allows administrators to remotely manage, audit, and wipe encrypted USB drives to ensure security and compliance within an organization.
How does SafeConsole enforce encryption on USB drives?
SafeConsole enables AES 256-bit encryption on all SafeConsoleReady™ USB devices, ensuring that sensitive data is protected both at rest and in transit.
Can I track the location of my encrypted USB drives?
Yes, SafeConsole provides geolocation tracking and geofencing capabilities, allowing administrators to pinpoint the location of USB drives and restrict their use based on geographic zones.
How can I reset a password on a USB drive remotely?
SafeConsole allows administrators to remotely reset passwords on encrypted USB drives without any data loss, helping users regain access to their drives securely and quickly.
What file types can be restricted on encrypted USB drives?
SafeConsole’s File Restrictor feature allows administrators to block certain file types from being saved on encrypted USB drives, such as EXE or MP3 files, to prevent unauthorized content from being stored.