Developed in 1998 by Vincent Rijmen and Joan Daemen, two Belgian cryptographers, Advanced Encryption Standard, or AES, has been around for several decades. Originally referred to as Rijndael, AES is symmetric encryption, meaning it uses the same key to encrypt and decrypt data. By using the substitution permutation network algorithm (SPN), it encrypts through multiple rounds. The length of these rounds is why this form of data security is so effective – there are simply too many rounds for a computer to process and crack.
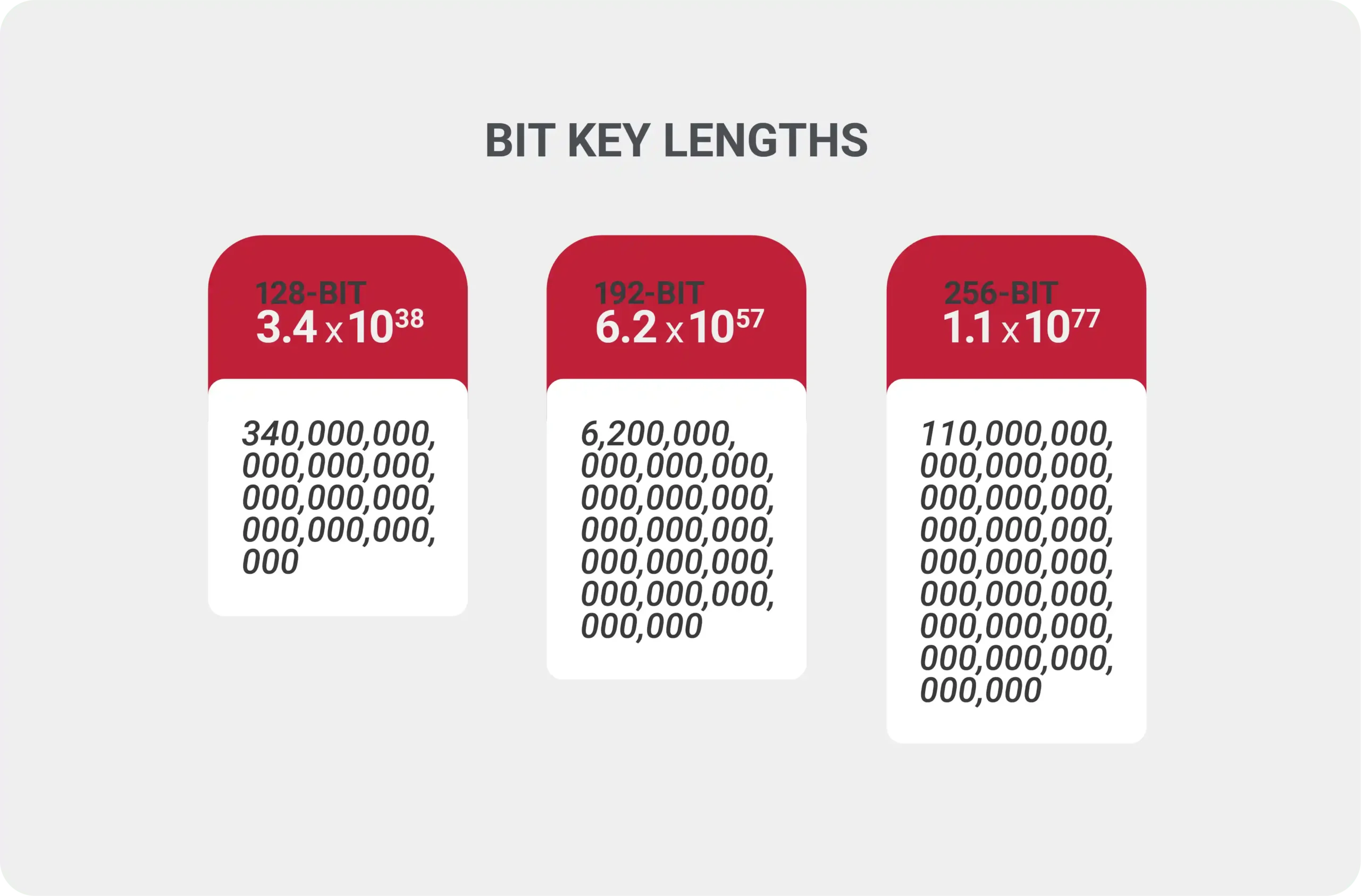
In AES, there are three different bit key lengths used: 128-bit, 192-bit, and 256-bit. Each key has a different range of possible key combinations. AES encryption will always have a fixed or base key length of 128-bit, referred to as its block size, but can be lengthened if more security is needed. Here is an example of how many different types of key combinations there are for each length:
The original Data Encryption Standard (DES) developed in the 70s only had a 56-bit key. In today’s world, some computers could crack this in less than 400 seconds, but the 128-bit would take a practical infinity of years to break.
Which One to Choose?
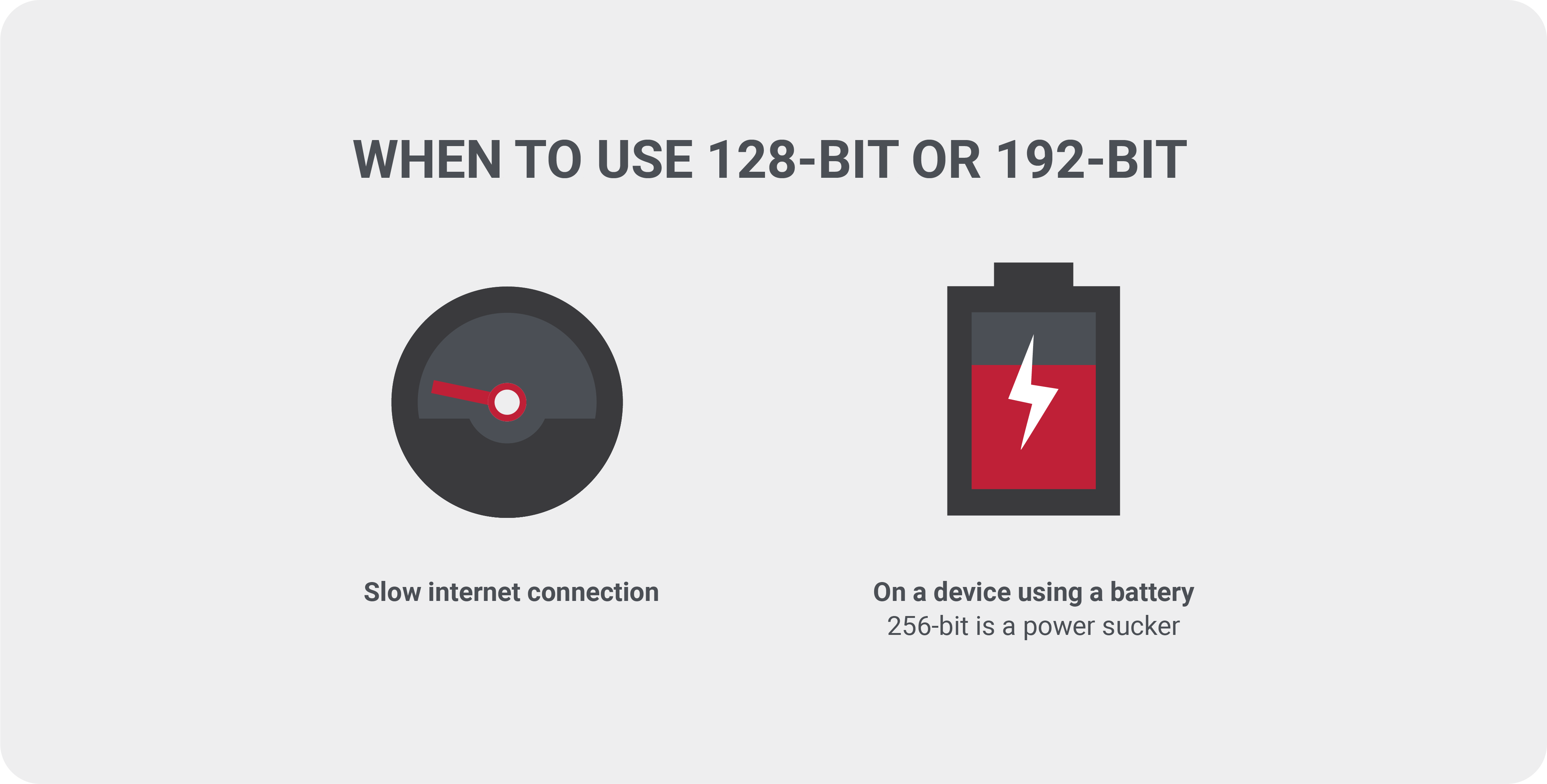
The 256-bit key often referred to as “military-grade,” is the most difficult to crack since it offers the most combinations. If this is the highest level of security, then why are the other options available? As with most things, it’s all about available resources.
As technology continues to advance and speed issues become less of a problem, using the 256-bit speed shouldn’t be much of an issue.
One of the strongest arguments for this type of encryption is its ease of use, making the implementation simple. It encrypts and decrypts quickly and is relatively easy to understand, using less memory than other types of encryption when combined with different levels of protection like a WPA2 or SSL.
Just imagine what time it would take to crack a 256-bit AES key, which boasts a staggering number of 984,665,640,564,039,457,584,007,913,129,639,936 combinations. Keeping this number in mind, we can safely assume that a brute-force attack on AES encryption will not happen without a significant increase in computing power.
Where is the AES Algorithm Used?
The short answer is all over the place, but it’s not everywhere – yet. As AES became the government’s go-to encryption cipher, it quickly became the encryption standard for basically anything we see online. As a result, you will have trouble finding industries or services that don’t use the AES algorithm.
Online banking credentials, passwords, and messages all need to be protected from people who can do harm. So, aside from “serving” the government (like the National Security Agency), the advanced encryption standard protects the sensitive data of a myriad of products.
The good news is that every day more and more companies are encrypting their information. The DataLocker team is committed to helping those companies keep data away from thieves trying to steal information. To learn more about our products and services, please reach out to our sales team at Sales@datalocker.com.