After succumbing to ransomware, businesses paid hackers an average of $84K to get their data back. And although the number of businesses reporting having been attacked by ransomware has gone down, it’s not because ransomware is happening less frequently. It’s because attackers are becoming more sophisticated and more targeted in their approach. Fewer businesses overall were attacked in 2020 compared to 2019, but orgs with higher value assets are being targeted since they can often pay heftier, sometimes multi-million dollar ransoms. No longer are they casting a wide net for small fish, they’re hunting for whales.

Though the cost to unlock data is high, so too are the related costs like employee downtime, impact to reputation and so on. The ransomware problem continues to grow, and organizations continue to be vulnerable. Luckily, there are a few tactics that can help prevent ransomware or even circumvent it should it find its way into your network.
Educate and Test End-Users
Try as you might to prevent nefarious emails and other attacks from entering your network, they’ll still weasel their way through. Which means you’ll be counting on even your least tech-savvy staff members to know the difference between a well-crafted spam email and something legit. That’s why many businesses hold regular cybersecurity trainings for their employees. These sessions help employees understand the latest cyber threats, help them spot illegitimate emails and requests, and reinforce company policies that help prevent things like social engineering. If you’re not already conducting similar classes, consider making it a priority. If you’re not sure how to build a curriculum, there are many online resources that can help inform your team. Last, consider using a fake phishing tool to test users and ensure that they’re being vigilant about messages that come their way.
Beef Up Basic Security
You’re no-doubt already using antivirus and anti-spam protection, VPNs, firewalls, and other network protection, but are you keeping all systems patched? The average business takes 12 days to apply a patch across all devices—that’s an awful long time for devices to be vulnerable to attack. If at all possible, try to prioritize security patches and apply them quickly. On top of that, consider upgrading the systems you already have. Be sure to regularly evaluate new vendors to see if there are more effective and comprehensive ways of protecting your network. If you’re not already doing so, reach out to contacts in users’ groups, read through forums, and read top security publications to find out what the latest and greatest tools are and try a few out.
Add Protection for External Storage
Ransomware is a fickle beast. It’s easy to forget that it doesn’t just lock up local drives on infected machines—it can lock up anything connected to it. Your external hard drive, thumb drives, and any external hardware can be affected by ransomware as well. That’s why it’s crucial to use external hardware that offers a little more than basic storage. Consider finding solutions that leverage encryption and can be remotely managed by your IT team. This will allow admins to set devices to read-only all the time, or when not connected to a trusted machine, preventing any data (including ransomware) from being written to the drive. On top of that, some storage solutions have onboard antivirus and antimalware, which can find, quarantine, and delete ransomware based upon policies that you define. This keeps ransomware from hopping on a USB stick and waiting patiently until it lands on another, more critical target.

Be Rigorous About Backups
If ransomware locks down equipment on your network, you’ll have little choice to pay the ransom—unless you have a backup. While most businesses have some form of backup, it’s not always built with ransomware in mind. If ransomware attacks your network and backups are stored on your network, your backups could be locked up as well, making them useless. As a safeguard, many businesses will make copies of backups to store at a second location, completely separate from their network. Businesses may also regularly replicate backups to a third-party cloud, where they’re safely away from local attack and ready to be used for recovery if they’re needed.
Get Cyber-Security Insurance
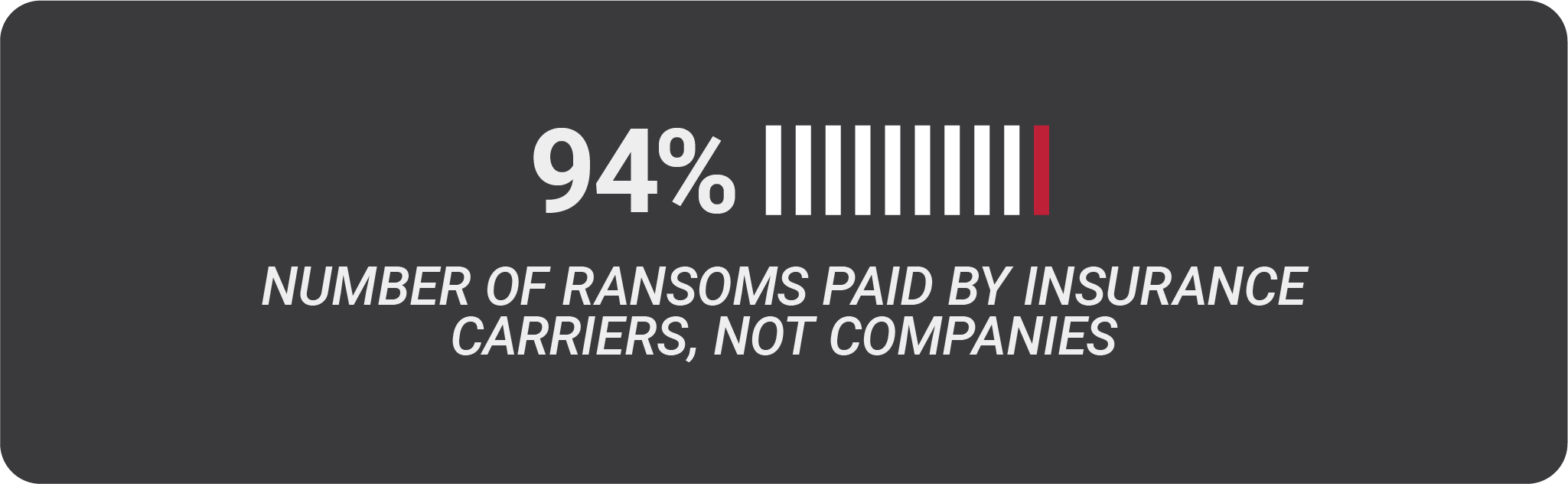
According to a report by Sophos, 94% of ransoms paid to cybercriminals aren’t paid by the company itself, but by the company’s insurance carrier. Your business might already have a policy covering things like ransomware and other cyberattacks, but it’s always wise to make sure your policy is covering everything you need. Check with your carrier to make sure your bases are covered, and if you don’t have a policy, get one. Most major carriers offer a plan that will keep you covered, and they’re relatively inexpensive. Also note that in some cases you can lower you cyber insurance costs by following best practices. You obviously want to do everything you can to prevent ransomware, but if you find yourself facing a hefty ransom, will you be able to pay or will you simply part with your precious data?
Conclusion
Ransomware continues to make headlines and though attacks are more sophisticated, it’s still preventable. Take a moment to consider whether you need to invest more in prevention, which could include education for your users or more complete threat detection solutions. Only then will your org be protected from ransomware today and in the future.